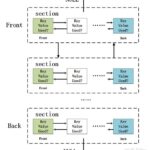
Monero’s ring signatures, stealth addresses, and RingCT ensure untraceable trades. In 2025, 95% of markets prefer XMR...
These sites cater to cybercriminals seeking valuable data, such as credit card numbers, login credentials, and personal...
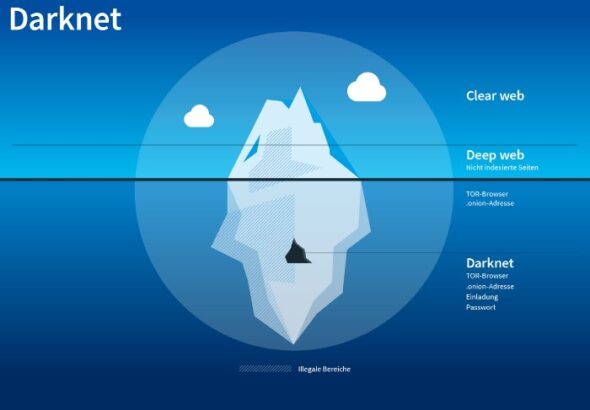
Therefore, the legality of the dark web will mainly depend on how you use it. You can...
The best markets in 2025 also prioritize vendor ratings and product diversity, allowing users to make informed...
Buyers benefit from access to a broader selection, ensuring they can find exactly what they are looking...
Even browsing these sites can put you at risk of malware infections or attract unwanted attention from...
Shop for exclusive products in our marketplace, where privacy, security, and anonymity are always a top priority....
Such models ensure that the market remains community-controlled and resilient to outside interference. Experienced blogger with a...
By following the guidelines outlined in this article, you can safely navigate the world of darknet markets...
Although the new forums were similar to the Breach forum, the fear that the new site was...