
This often includes a “checker service,” a compromised merchant account they use to run dinky charges through to see if the card is still valid, Krebs says. If someone agrees to use the shop’s checker service instead of a third party, the shop will give a guarantee that at least a portion of the cards are usable for a certain period of time. Many tracker apps link directly to bank accounts for up-to-the-minute info.
- Post the dismantling of Joker’s Stash, cybercriminals displayed adaptability by establishing new marketplaces to fill the void, highlighting the resilience of criminal enterprises.
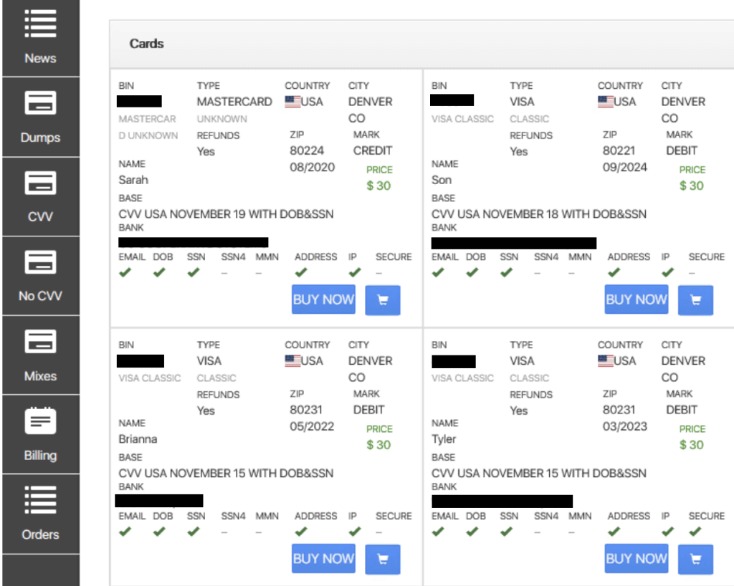
- The first leak offered only the information contained in magnetic stripes of compromised cards, while the latest sale includes fullz – card number, expiration date, CVV/CVC, cardholder name, and extra personal info.
- When we spot cards from these BIN ranges appearing in bulk listings, it often indicates a breach somewhere in the payment chain.
- The dark web may be an ever-present undercurrent, but with the right strategies and awareness, you can navigate the digital landscape confidently and securely.
- Passionate about blending creativity with functionality, Alex specializes in crafting visually compelling websites that drive results.
The pricing varies based on the card type, with premium cards from certain banks fetching higher prices. A fair number of vendors include access to a SOCKS5 internet proxy that can be used by the buyer to match their computer’s IP address location with that of the cardholder in order to avoid being blacklisted. Experience Flare for yourself and see why Flare is used by organization’s including federal law enforcement, Fortune 50, financial institutions, and software startups. For instance, BidenCash saw a surge in user activity following its free data leaks. This tactic mirrors similar marketing stunts by other illicit platforms, such as BidenCash, which leaked 2 million cards in 2024 to celebrate its anniversary. Once they had access to the victim’s account info, scammers would estimate their wealth to gauge the types of purchases they could make with the card.
What To Do If Your Information Is Found On The Dark Web
Verified by Visa is a service that prompts the cardholder for a one-time password whenever their card is used at participating stores. The average price of a cloned, physical card is $171, or 5.75 cents per dollar of credit limit. Comparitech researchers sifted through several illicit marketplaces on the dark web to find out how much our private information is worth.
- Knowing about the dark web credit card reality is essential with this alarming crime rate.
- In a nutshell, the deep web is a high-security world, almost like a vault filled with precious data.
- For questions or concerns, please contact Chase customer service or let us know about Chase complaints and feedback.
- Sales of passports, driver’s licenses, frequent flyer miles, streaming accounts, dating profiles, social media accounts, bank accounts, and debit cards are also common, but not nearly as popular.
- Valued at approximately $15 million, Abacus Market is one of the most lucrative platforms in the dark web ecosystem.
- The BidenCash stolen credit card marketplace is giving away 1.9 million credit cards for free via its store to promote itself among cybercriminals.
Protective Measures And Precautions

The process, also called skimming, allows them to make physical purchases at ATMs or retail stores. Unlike online fraud, this type of theft is harder to detect because the transaction appears as a regular swipe. These details often land there after data breaches, phishing attacks, or malware infections that steal information from unsuspecting users.
Stolen Credit Card Numbers—A Guide To Safeguarding Your Funds

And what’s worse, this shady corner of the internet is only getting bigger. Strong passwords and security tools add extra layers of defense against cyber threats. Discover the pros and cons of using credit cards or card for purchases, including benefits and risks, to make informed financial decisions. Card checkers are tools used by threat actors to verify the validity and authenticity of credit card information they purchase on the dark web. Established in 2019, Russian Market is a well-known and highly regarded data store on the dark web, specializing in the sale of PII and various forms of stolen data. Despite its name, the marketplace operates primarily in English and serves a global audience.
What Role Do Cryptocurrencies Play In Dark Web Transactions?
Stolen credit card details can be categorized into different types, making it easier for cybercriminals to exploit them. It is a hub for financial cybercrime and offers a wide range of illicit services and stolen data that cater to sophisticated cybercriminals. Thegrowing prevalence of NFC in everyday transactions underscores theurgent need for stronger security measures, enhanced fraud detectionsystems, and global cooperation to combat this rising threat.
Public Data Breaches
Dark web credit cards are often sold in bundles, with hundreds or even thousands of credit card numbers available for purchase. The Google hacks, popularly known as Google dorks for credit card details,48 are also used often in obtaining credit card details. Two other states had indictments for Roman Seleznev and wanted to try him, too.
Regular Credit Monitoring
Exploring the realm of credit card transactions on the Dark Web is a journey into a dangerous and illegal world. While the allure of cheap credit card details and the potential for financial gain may be tempting, the risks and consequences of engaging in such activities cannot be ignored. Stolen credit card details are sold for a fraction of their actual value, making it an attractive option for fraudsters looking to finance their criminal activities. Welcome to the dark underbelly of the internet, where secrecy reigns and illicit activities thrive. The Dark Web, a hidden part of the internet accessible only through specialized software, is a hub for illegal transactions, including the buying and selling of credit cards. If your credit card information is compromised, report it immediately to your bank, monitor your accounts for suspicious activity, and consider using a credit monitoring service.

In this post, we’ll cover how credit card fraud operates on the dark web, how criminals obtain and trade card data, and cover some essential prevention strategies. Hijacking a PayPal account requires a different approach than stealing a credit card number. Instead of card numbers and CVVs, criminals steal usernames and passwords that they’ve gathered either through phishing or malware. They can then sell the account credentials to a buyer who can log in and drains the funds, or the vendor can transfer the requested amount of money from the victim’s account to the buyer’s account.
If you notice suspicious activity, you can pause or close your virtual card in a few clicks—–via either Privacy’s web app or mobile app—and Privacy will decline any subsequent payment requests on the card. You won’t have to block and replace your actual payment card, which is often a complicated and lengthy process. She combines her background in digital marketing from DePaul University with a passion for cybersecurity to create content that helps people and businesses stay secure. Her writing covers everything from password best practices to Privileged Access Management (PAM), with a focus on making technical topics easy to understand. Here are some tips to keep your credit card information safe from compromise in the future.
It can take months—or even years—to recover from this kind of identity fraud. More bogus credit card data, personal information, and documents were sold in 2021 compared to 2020, while products, like hacked cryptocurrency accounts and web services such as Uber, are more available. Monitoring your credit is crucial in protecting yourself from credit card fraud on the dark web. By regularly checking your credit reports and statements, you can quickly identify any unauthorized charges or suspicious activity. Look out for unfamiliar transactions or sudden changes in your credit score. If you notice anything unusual, contact your credit card company immediately to report the issue.

Network segmentation is absolutely critical for businesses handling card data. One particularly interesting detection method involves monitoring dark web markets themselves. Financial institutions tighten their security measures to prevent fraud but that also prevents legitimate transactions as a result. They invest massive resources into fraud detection systems, customer service teams dedicated to handling compromised cards, and the logistical nightmare of card reissuance.
Now, the market’s operators decided to promote the site with a much more massive dump in the same fashion that the similar platform ‘All World Cards’ did in August 2021. According to Kaspersky expert Sergey Shcherbel, the actual number of devices infected by infostealers is most likely higher. Check out the Chase Auto Education Center to get car guidance from a trusted source.
He has advised numerous international organizations, public and private sector entities on future crime issues. In addition to being a welcome further blow against an already struggling criminal enterprise, the story of Yale Lodge offers interesting insights into the dark web carding ecosystem. As previously mentioned, credit card fraud is a massive market for criminals. According to data from Merchant Savvy, global payments fraud has increased from $9.84 billion in 2011 to a staggering $32.39 billion in 2020. The illegal carding market, which can be accessed through the dark web, went live during June, 2022.
Once a scammer has their hands on your credit card information and is ready to use it, they may start small. The idea is to check if the credit card works first by charging an inexpensive transaction, often for less than $5. Dark Web ID has been an industry leader for years because they never stop innovating to keep businesses out of credential compromise trouble. Arda is a Senior Crypto Threat Analyst at Elliptic with a focus on crypto-based terrorist financing, dark web vendors, NFTs and DeFi-related crime. He is also a PhD researcher and guest lecturer at the Dawes Centre for Future Crime at University College London (UCL), focusing on the money laundering and terrorist financing risks of emerging technologies.



