Plus, controlling access to the dark web would be a massive undertaking. PrivateVPN allows torrenting and has dedicated servers in its home country for just that purpose. Torrenters can also make use of port forwarding, which allows connections to more peers in a torrent swarm.
How Do I Access Tor?

Ensure you have used prepaid and unidentifiable credit cards when purchasing on the dark web. Avoid using payment methods that can easily expose your identity. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings.
Can Malware Be Present On The Dark Web?
In fact, there have been instances where attackers controlled hundreds of Tor nodes. The Deep Web includes unindexed content like private databases and password-protected sites accessible with standard browsers. Many people use it for privacy-focused communication, whistleblowing, or accessing restricted information in censorship-heavy regions. Platforms like SecureDrop even allow journalists to receive tips anonymously. This one also filters illegal content and is designed solely for the dark web. Ensuring user anonymity, Not Evil has no ads, web tracking and presents lower risks of malware attacks.
How To Get On The Dark Web Safely FAQs
The first step is to download and configure the Tor browser from its official website. The Tor browser is your gateway to the dark web, allowing you to access .onion sites anonymously. PrivateVPN is another relatively unusual provider in that it offers the VPN Over Tor configuration. The company’s website provides detailed instructions on how to use it. Again, we don’t recommend this method, though it might be preferred if the security of Tor exit nodes is of concern.
Tweak Tor Browser Settings
It connects you to a network of servers rather than a particular server. This makes it slower than a VPN and also very difficult to try and get a new IP address in a specific country, which is easy to do with a VPN. Because the Tor network is run by volunteers, there’s also little in the way of accountability. Bad actors can compromise nodes, with exit nodes being of particular concern.
Application Security
- It’s designed as an environment to elude detection, where site owners and visitors hide their identities.
- Since all activity on the dark web is anonymous by default, it is definitely where the murkiest transactions on the internet take place.
- Businesses may use these services to sabotage their competitors, while individuals may seek revenge or simply want access to private information about someone.
- The dark web, an even more puzzling sublayer, exists within this hidden world.
- From cybersecurity researchers to IT managers, understanding how to navigate the dark web can help monitor cyber threats, protect sensitive data, and investigate cybersecurity incidents.
Note that Tails’ installation package is the .img format, which means that you’ll need software capable of burning images on your thumb drive. As I’ve previously said, it’s a good idea to keep your interactions with the dark web to a minimum, unless you can absolutely trust the people you’re dealing with. You’ll often see a sign in stores that says “look, don’t touch,” and it’s not a bad adage to bear in mind as you navigate around the dark web.
Exiting Safely
So don’t be surprised if you encounter different versions that claim to be genuine, and be very careful. The Dark Web and Darknets offer valuable spaces if you value privacy, freedom of speech, or research security technologies.If you misuse them, the consequences can be severe. Unlike the Deep Web, Darknets are intentionally hidden and designed to preserve privacy and anonymity. Even platforms like Netflix, which require paid access, are technically part of the Deep Web.
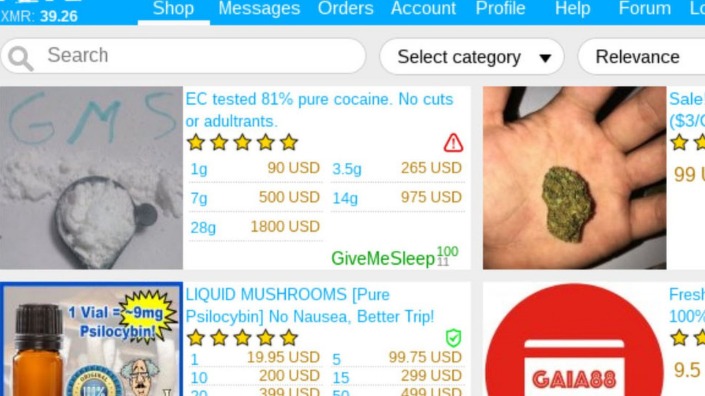
It’s also a marketplace for digital mercenaries; you’ll find everything from solo hackers offering their skills to well-organized groups that take on more complex or high-stakes projects. Some even have connections to criminal organizations and, in more serious cases, government-backed operations. But somewhere between production and purchasing, things can get dirty. For example, an insider or factory employee might quietly slip away with an unmarked gun and sell it online. Once it lands on a darknet marketplace, it becomes part of the illegal weapons trade.

Everything You Need To Know About The First Dark Web Market: The Silk Road Website
- Try LifeLock free for 30 days to receive notifications if we find your personal information on the dark web and help protect against identity theft.
- Successfully navigating this hidden world requires preparation, vigilance, and a thorough understanding of both the technical and ethical challenges at play.
- Think of your email inbox, banking dashboard, cloud documents, subscription content, or internal business tools.
- Being cautious while browsing the dark web is essential, as significant risks are involved.
- Regular dark web visitors know that it’s possible to exploit the sketchy reputation of the space and the services offered.
- It has billions of sites and addresses, it is amazing that we can both search for – and find – anything.
For this reason, you do use this app to connect to the dark web at your own risk. Sites often have simple black or dark-themed backgrounds and minimal design elements. Do not log into any of your personal accounts, such as social media platforms, email inboxes, or bank accounts, when exploring the dark web. Before we look at how to access the dark web, it’s important to have a thorough understanding of what it is, as there are many misconceptions about it. Indeed, most nations; including the United States, the United Kingdom, and India, allow access to the dark web as a lawful activity.
While visiting any of the sites you find on those Wiki sites, do not maximize your browser, as it can help identify you by your monitor resolution. DefCon, ProPublica, the CIA, various libraries, and open-source software providers also feature in this area of the internet. A VPN and Tor should be used together and it is advisable to connect via a VPN to Tor, rather than vice versa, for the best protection possible.
The users on this site can review and rate the products that promote reliable and fraudster vendors. Though not entirely shoddy, the dark web has a reputation for hosting illegal activities. It does support whistleblowers by offering them anonymity and secure communication in an oppressive regime. But navigating the dark web is full of cybersecurity and legal challenges.
Since these have been used several times for criminal offences and rampages and the media have reported on them, the darknet has increasingly become the focus of public attention. When you purchase through links in our articles, we may earn a small commission. We’re a nonprofit organization and rely on supporters like you to help us keep Tor robust and secure for millions of people worldwide.