Radar Rundown Ad blockers are the best protection against disruptive ads. While they might sound the same, these websites are fundamentally different. Read about the adventures of modern-day explorers who have made it their mission to venture into the tunnel network of huge American universities. The site is different from our whole list, but still worth a mention. Still, while the latter has a large digital collection of comic books, the Imperial Library has a large collection of books.
The Escrow Process
On the Tor network, the onion domain name reflects the fact that, like the layers of an onion, the Tor browser consists of layers of protection. Tor encrypts traffic, masks your IP address, blocks trackers and browser fingerprinting, and doesn’t store a record of your activity. Riseup is a volunteer-run social movement organization that offers email, email lists, a VPN, online chat, and other online services for political activists engaged in various causes. Riseup’s services can be accessed on the surface web or via Tor websites if users want to protect their anonymity. The darknet version of DuckDuckGo is not a search engine for the dark web, but a private browsing tool for the dark web.
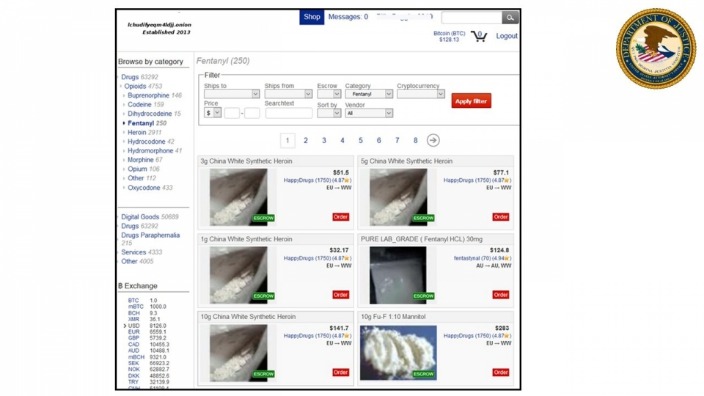
For those needing an additional layer of security, you can set it to disappear right after viewing. It has successfully become a replacement for AlphaBay Market, which was once leading the dark web transactions space. However, we do not recommend using this platform without taking proper precautions, such as anti-malware and a VPN. You can also use it on the surface web, but it is still unadvisable without proper safety measures. It has a vast library of over 1.5 billion indexed pages that lets you find whatever you are looking for.
Top 5 Deep Web Black Markets
University of Edinburgh student Ian Clarke created Freenet as a thesis project. Freenet was originally intended to provide a way to anonymously interact online, providing ways to communicate, exchange information and files, and to otherwise communicate incognito. The majority of the web is called the “deep web” (often referred to as the “invisible” or “hidden” web). The deep web is basically all the content that you can’t find using Google or Yahoo search. Typically, any reference to the visible web will be to common websites with a familiar internet domain extension.
The Fall Of Silk Road And The Rise Of New Marketplaces
The Hidden Wiki is one of the easiest ways to find useful resources and websites on the Dark Web. It is essentially a list of all the notable websites available on the Tor Network that is kept in a single, organized place. For this reason, it is always better to use a trustworthy VPN for Tor while accessing the Dark Web, as this will provide a robust additional layer of privacy. The Tor network is designed to provide you with privacy and anonymity.
Nowadays, many people use the Tor browser to surf the public internet and navigate the deeper parts anonymously. With the onion browser, you can access ordinary HTTPS websites on the web. This is a great way to improve your privacy because Tor isolates each website you visit, meaning third-party trackers and ISPs can’t reveal your identity. Keep in mind that you’ve to use very specific keywords when searching. And most importantly, be patient as you’ve to sort through a lot of useless results. These search engines work best if you already know what site you’re looking for, not for general browsing.

Access The Dark Web Safely

One of the most well-known technologies enabling darknets is the Tor network, which was developed by the U.S. Naval Research Laboratory in the mid-1990s and later released to the public. Tor, short for “The Onion Router,” routes internet traffic through a global network of volunteer-operated servers to anonymize a user’s online activity. This technology initially had noble intentions, aiming to protect activists, whistleblowers, and individuals in repressive regimes. However, it soon became a double-edged sword as malicious actors began to exploit its capabilities for illicit purposes.
Accessing Onion Sites On Android

The darknet is a mysterious and often misunderstood part of the internet, attracting both intrigue and concern. Darknet markets, in particular, have gained attention for their role in facilitating the exchange of illicit goods and services. Despite their controversial nature, these marketplaces continue to evolve, offering a glimpse into the darker side of online commerce. As cyber threat intelligence professionals monitor these markets, they gain insights into emerging threats and malicious activities that can impact organizations and individuals.
Why Monero Over Bitcoin?
Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for. You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe. The dark web comes with its own set of tools and services, including web browsers and search engines (which I’ll get on to in a moment).

Tor Metrics
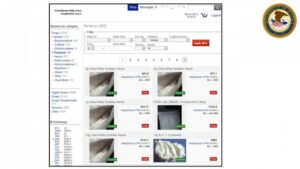
It allows you to buy and sell a wide range of products and services with a good user experience. This site supports PGP encryption and two-factor authentication features. These are the primary sources of what the general public thinks of as “dark web.” Online marketplaces selling hacked credit cards, fake passports, malware kits, untraceable drugs, anything. Another website is Dread, which is often called the “Reddit of the Dark Web.” It’s a community platform where users can discuss new markets, share onion links, add reviews, and much more. If you’re lucky enough, you can find it on clearnet privacy forums. Blockchain even has an HTTPS security certificate for even better protection.

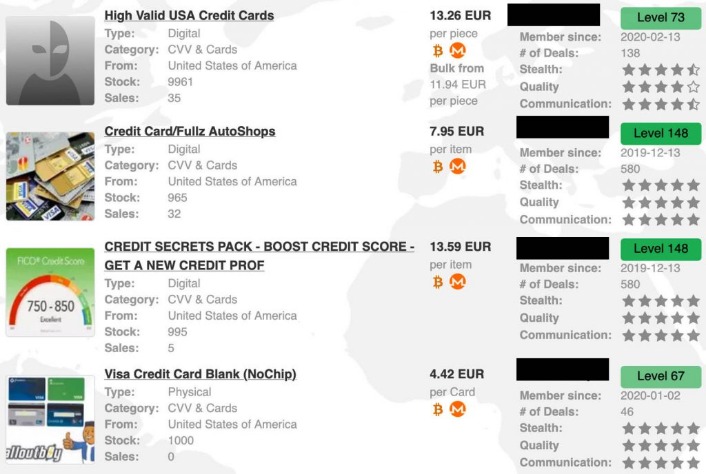
FreshTools, founded in 2019, specializes in selling stolen account credentials and data, particularly webmail, RDPs (Remote Desktop Protocols), and cPanels. The marketplace requires merchants to pay fees to sell their products, helping ensure a certain level of quality control. Its user base is primarily English-speaking, and it appeals to more sophisticated cybercriminals. Here’s a look at the top 10 dark web markets currently dominating this underground space. Operation RapTor involves law enforcement actions taken by JCODE member agencies, including the DEA, FBI, FDA OCI, HSI, IRS-CI, and USPIS.
- This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks.
- It’s not as massive as Abacus, but quality’s on point—vendors deliver, and the community’s buzzing on Dread about it.
- The sites also accepted payments for their illicit goods and services in bitcoin or similar virtual currency designed to be as anonymous.
- The good thing about Haystak is that it tries to filter out dangerous sites from your search results.
How To Protect Your Identity While Browsing The Dark Web
Popular news publications like The Washington Post, The Guardian, TechCrunch, and more have set up their own SecureDrop URLs so whistleblowers can contact them effortlessly. SecureDrop claims that all the messages you send and receive are encrypted in transit to prevent third parties from intercepting them. For obvious reasons—I don’t want to get you or me into trouble, after all—I’m not going to get too specific when it comes to what you can find for sale on the dark web. A lot of transactions are handled via cryptocurrencies such as Bitcoin, which is relatively (but not completely) private and anonymous. Another private cryptocurrency you’ll find being used is Monero, which prides itself on being untraceable.
In addition, several fake websites impersonate the famous dark net marketplace to obtain your financial and personal information and use it for malicious purposes. Onion sites aren’t really dangerous, but they could be when accessed through unfamiliar or suspicious links. The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for. This solution focuses on identifying stolen data, brand misuse, and potential threats before they can cause significant harm.