Early detection enables your security team to prevent a transaction, minimizing the risk of a chargeback. Require multi-factor authentication for high-risk transactions, but it needs to be implemented intelligently. Pattern recognition through machine learning has revolutionized how we spot compromised cards. I’ve worked with family-owned businesses that nearly went under after getting hit with a wave of fraudulent purchases. When fraudulent transactions occur, merchants frequently end up eating the costs through chargebacks. The Magecart group pioneered this technique, compromising thousands of online stores by exploiting vulnerabilities in popular e-commerce platforms.

This kind of network is typical for hackers to monitor your activity and capture your credit card number during transactions. Malware can be installed on your device through suspicious downloads, pop-ups, or phishing scams. Once installed, this software can track your keystrokes or gain access to your saved credit card information. This password unlocked access to credit histories and personal information, which could be used to obtain credit card numbers. In 2019, hackers infiltrated a major credit card processing company, compromising over 1 million credit card numbers. Experian’s free credit monitoring service is one easy way to stay alert.

Using a list of 500 million email addresses, they identified over 15 million users and compiled data including email addresses, names, usernames, and activity logs. In January 2024, Indian ISP Hathway was breached by a hacker known as “dawnofdevil,” exploiting a vulnerability in the Laravel framework. While the attacker claimed access to data of over 41 million customers, analyses suggest approximately 4 million unique records were affected.
Don’t Fall Prey To Identity Theft
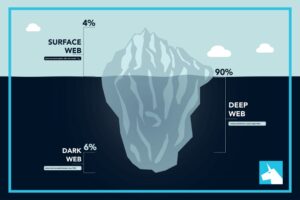
The sooner you become aware of compromised information, such as stolen credit card numbers on dark web, the faster you can take steps to mitigate damage. Rapid response can prevent unauthorized transactions, minimize financial losses, and protect your customers’ trust in your business. Only through collective efforts and advancements in cybersecurity can we hope to mitigate the impact of these nefarious activities and safeguard the digital landscape for future generations. The dark web market is growing, with retailers selling stolen credit card data, cryptocurrency accounts, hacked Gmail and Twitter accounts, and purchasable malware for significantly cheaper prices over the past year. Some have fresher cards that were just stolen yesterday so finding good credit card dump vendors is highly sought after.
AT&T Data Breach Via Snowflake
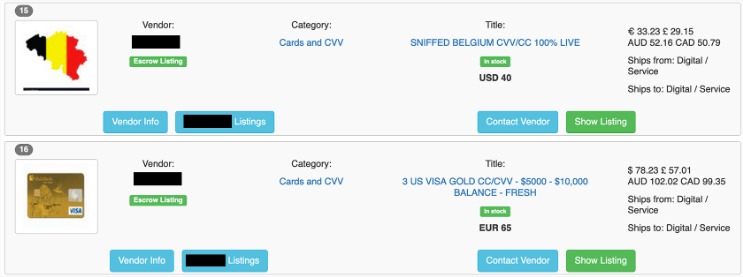
The data dump disaster includes some complete names, expiration dates, CCV and unique email addresses. Detecting and preventing dark web credit card fraud can be difficult since the dark web is, by nature, hidden. By using specialized tools cybersecurity professionals can track these illegal activities and alert financial institutions of potential threats. This article will explore credit card theft on the dark web, explain how criminals obtain and use stolen data, and explain how to detect and prevent credit card fraud. These aren’t just random forums, they’re organized platforms where stolen card data gets packaged and sold as “fullz” (full card details including CVV) or “dumps” (raw magnetic stripe data). Leaked credit cards from Telegram channels account for the overwhelming majority of compromised payment card details.
Technical Details And Data Sources
The incident, disclosed in its Q3 earnings report, continues to disrupt fulfillment and supply operations. Mador recommends that merchants carry out penetration testing, via a third-party security company, to scan websites and applications on an ongoing basis. “We report when we see security issues—missing patches, nonsupported software, or using out-of-date versions of programs,” and then recommend steps for remediation.
From technological solutions like payment card BIN monitoring to simple practices like monitoring your financial statements, the key to protection lies in proactive and informed action. Protecting yourself from these threats requires a combination of personal vigilance and technological assistance. A 2018 special report from Vice shows an anonymous scammer browsing stolen credit card numbers on the dark web. He chooses one, stamps the number and information onto a blank card, and uses that card to make payments, often using the stolen payment information to buy goods, like gaming systems, and sell those as well. Hijacking a PayPal account requires a different approach than stealing a credit card number.
Enhance Your Threat
In contrast, breaches of CNP data rose from 18 percent to 25 percent in that same time period. When you add your credit card number for monitoring, it is encrypted before being sent to our servers. Once received, we securely store it using SHA (Secure Hash Algorithm) to safeguard your personal data. These services scan the dark web to see if your personal information, such as credit card numbers, appears online.
- Full or partial credit card details, also known on the dark web as CVVs and CCs.
- The cybersecurity community is on high alert as B1ack’s Stash, a known marketplace on the dark web, has announced a massive leak of 4 million stolen credit card details.
- According to the United States Attorney’s Office, the ring of thieves obtained the credit card information on the dark web, and used that information to create their own cards.
- Let’s start right out with a step-by-step overview of the whole process, and then we’ll dive into some of the specific tools and methods that cybercriminals use in more detail.
- Credit card prices also vary depending on the brand, with American Express being worth the most at 5.13 cents per dollar.
- In February 2025, Western Sydney University experienced a data breach that compromised the personal information of approximately 10,000 current and former students.
Individuals
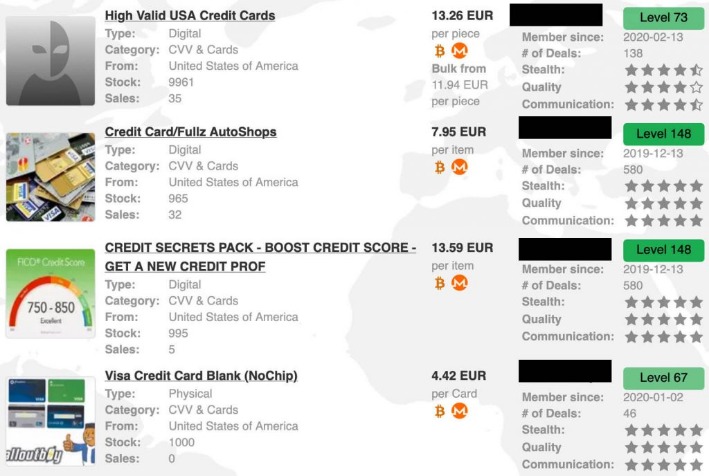
There are also scammers that advertise using stolen cards recycled from other sources, entice people to buy a fake premium offering, take their money, and then never deliver any additional data. A Russian-language dark web shop known as BidenCash recently attracted attention from cybersecurity researchers by posting a leak — for free — of 2 million stolen payment card numbers. A dark web carding market named ‘BidenCash’ has released a massive dump of 1,221,551 credit cards to promote their marketplace, allowing anyone to download them for free to conduct financial fraud. With so many ways for thieves to steal your credit card information, it’s more important than ever to stay vigilant.
Curious About How Breachsense Can Help Your Organization Detect Credit Card Fraud? Book A Demo To Learn More
If your card is linked to auto-pay services or has a high spending limit, the damage can escalate quickly—often before your bank even flags it as suspicious. In early 2024, American Express notified customers of a data breach originating from a third-party merchant processor. The breach exposed cardholder names, account numbers, and expiration dates of over 50,000 customers. In April 2024, Pandabuy, a Chinese e-commerce platform, suffered a data breach compromising the personal information of approximately 1.3 million users. The breach included names, contact details, order information, and addresses.
Detecting Fraudulent Activity On Your Accounts
In an increasingly digital world, the threat of data breaches looms larger than ever. From multinational corporations to individual users, no one is immune. In some cases, cybercriminals leak the data they obtain on the dark web for free to threaten the victims in case they don’t receive the demanded ransom. If your credit card is found on the dark web, change related passwords, report it to your bank, request a new card, and monitor for suspicious activity.
The leak was shared free of charge as a promotion to the threat actor’s new carding marketplace, named AllWorld Cards. In recent years, I’ve observed some shifts in how carding is carried out—changes that mirror broader developments in both technology and threat intelligence research. Notably, cryptocurrency has become a valid option for carding operations, whether through exploiting stolen crypto wallets and accounts or using stolen credit card details to purchase cryptocurrency.
The vast majority (98% of the records) came from Indian banks, Group-IB said in its threat report. The source of the payment card batch, which went on sale on the Joker’s Stash on Wednesday (February 5), remains unconfirmed, although circumstantial evidence suggests it came from online theft. Card cloning involves creating a replica of a credit card using the stolen information, which can then be used to make purchases or withdraw cash.
How Do Attackers Obtain Financial Data?
AllWorld.Cards appears to be a relatively new player to the market for selling stolen credit-card data on the Dark Web, according to Cyble. “Our analysis suggests that this market has been around since May 2021 and is available on a Tor channel as well,” according to the post. When a hacker writes up new malware, steals a database, or phishes someone for their credit card number, the next step is often toward dark net marketplaces. These black markets allow buyers and sellers to make anonymous transactions using a combination of encrypted messages, aliases, and cryptocurrency.