The extent of the problem became clear in 2015, when the FBI shut down a dark web site on Tor named Playpen that hosted 23,000 sexually explicit images of minors. Not all mass thefts of data facilitated by the dark web have been motivated by money. The publicizing of Snowden’s actions led to a global spike of interest in Tor and a resulting rapid expansion of the network’s user base. Law enforcement officials are getting better at finding and prosecuting owners of sites that sell illicit goods and services.
The dark web is a secret network of websites that can only be accessed with a specialized web browser. It is used to maintain the privacy and anonymity of online activity, which is useful for both authorized and illegal purposes. The accessibility of it for potential criminal activities has also been reported, even though some people use it to avoid government censorship. The Dark Web is a component of the internet that is not indexed by traditional search engines and requires special software to access. It’s where illegal activities occur and is home to some of the most dangerous elements of the online world.

Hidden Answers
No, simply accessing the dark web using Tor or other anonymizing browsers is not illegal. However, engaging in illegal activities on the dark web, such as viewing child pornography, selling drugs, or participating in other illicit transactions, is against the law. It is important to differentiate between the tool (Tor) and the actions performed using that tool. The dark web often carries a negative connotation, largely due to its association with illegal activities. However, it also offers significant advantages, especially in terms of privacy and security.

Start The Tor Browser
While it might appear tempting to venture into the dark web, it’s crucial to understand that the risks here are far more severe compared to the deep web. No one is hiding here—they’re just guaranteeing that people in censored countries can read the news without being flagged. Hence, you never know when a popular .onion site is going to vanish, or even die.
It operates on a hidden network, requiring tools like Tor to navigate its unique structure. Matt Egan is Global Content Director of Foundry, publisher of Tech Advisor, and a passionate technology fan who writes on subjects as diverse as smartphones, internet security, social media and Windows. The content management system into which I am typing this article is on the Deep Web.
What’s On The Dark Web?
When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI. The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers. The dark web is infamous for containing sites such as Silk Road and other marketplaces where users could potentially buy drugs and/or weapons, stolen credit cards, IDs, and much more. The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose. The content of all these pages is stored on Google’s servers, but it’s mostly outdated, old content; smartphone app content; journals; court records; private social media profiles, and much more. By integrating top-grade security into their operations, organizations can not only reduce their exposure to cyber threats but also reinforce trust in an increasingly data-driven world.
If The Dark Web’s Secret, How Does Anyone Find Anything?
These services scan hidden sites and leaked databases for your information. If they find your details, you’ll get an alert along with steps to help you respond — like changing passwords, freezing your credit, or monitoring for identity theft. The dark web is a hub for ransomware tools and phishing kits that criminals sell or rent to launch attacks on people like you. Illegal software, fake documents, and hacking services are all part of this underground market.
Advantages And Disadvantages Of The Dark Web

Tor (“The Onion Routing” project) network browser provides users access to visit websites with the “. This browser is a service originally developed in the latter part of the 1990s by the United States Naval Research Laboratory. Drugs are typically sold using cryptocurrency to maintain anonymity, and the buyers and sellers are often difficult to trace. These markets operate similarly to physical drug markets but are hidden from law enforcement through the use of the Tor network.
While Bitcoin and other cryptocurrencies provide some level of anonymity, blockchain analysis tools can trace illicit transactions. Organizations like WikiLeaks and investigative journalists use dark web platforms to exchange sensitive information safely. In this guide, we’ll show you what you need to know about how to access the dark web and how to keep yourself safe while you use it. The dark web hosts a wide array of content—some of it perfectly legal, some ethically gray, and some outright illegal.
Use A Trusted VPN
- Services such as Tumblers are also available on the dark web to help hide transactions.
- Tor Browser versions for Android and iOS allow smartphone users to access.onion sites.
- Gannicus Oliver is an experienced tech journalist (he loves writing on emerging techs and digital privacy issues) and an online business consultant.
- Facebook offers an onion link to access their services, although you may find logging in difficult, as you’ll most likely appear to be signing in from a different location each time.
- By approaching this hidden corner of the internet with informed caution and ethical awareness, you can navigate it more safely and responsibly.
The Silk Road was especially known for its role in the online drug trade but was host to other illegal transactions until it was shut down by the Federal Bureau of Investigation in 2013. To access a dark web address, you must use a VPN and a suitable browser (it should be Tor). The aim is to reduce your online footprint as much as possible, anonymize your traffic, and disguise your location.
ExpressVPN had created a .onion version of its website to allow greater privacy and anonymity for Tor browser users. You don’t need special tools or a special browser like you need to access the dark web (more about that later). Anyone can access the deep web by using specialized search engines, dedicated web directories, and other sources that can help you find the data or information. Hidden, encrypted and out of reach of traditional search engines, the dark web is a place where anonymity rules. Users slip into this shadowy realm using a anonymizing browser, like Tor (The Onion Ring) browser, and a Virtual Private Network (VPN) to protect their identity and secure their connection.
- Believe me – there are plenty to go around and each and every one of them are being kept under surveillance.
- There’s a significant risk to dark web users of being exposed to malware (malicious software) infections.
- Because of the built-in anonymizing features and encryption, the Dark Net is also host of many criminal websites, marketplaces and networks.
- For anyone considering exploring the Dark Web, it’s crucial to tread with caution.
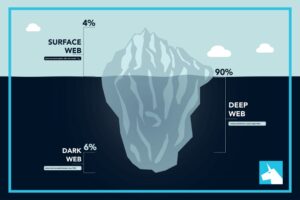
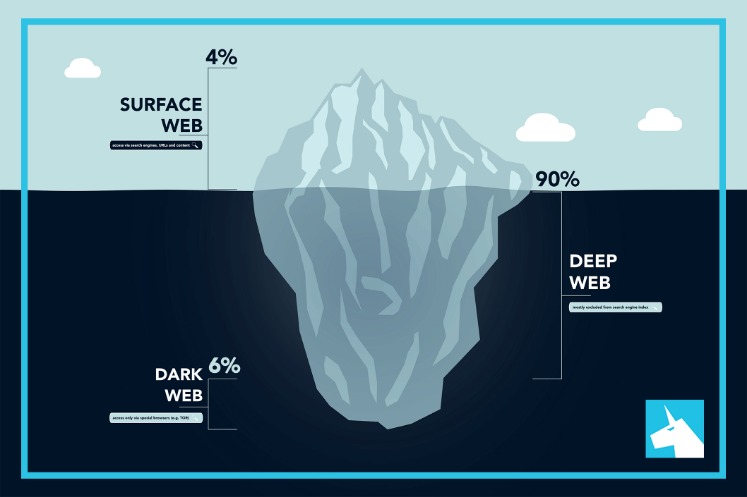
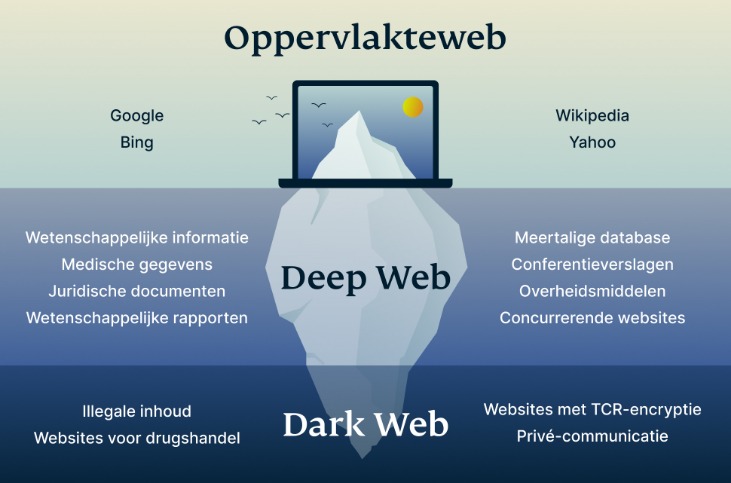
Beneath this surface lies the deep web, encompassing private databases, subscription-only services, and other non-indexed content. Within the deep web is an even more hidden layer known as the dark web, accessible only through specialized browsers like Tor. The deep web is significantly larger, accounting for approximately 90–95% of online content. Unlike the surface web, it consists of pages not indexed by standard search engines. Examples include password-protected databases, academic research repositories, and private corporate networks. These are legitimate resources that remain hidden for reasons such as privacy or security.

Sure, you can use other cryptocurrencies if Bitcoin’s not your cup of tea. You should stay away from everything labeled “porn”, “card skimming services”, “PayPal hacks”, “firearms”, “real fake IDs and passports”. Believe me – there are plenty to go around and each and every one of them are being kept under surveillance. Not to mention the fact that you’ll get exposed to some stuff that will definitely make you take several cold showers.
Corporations and governing bodies alike currently participate in unauthorized surveillance of online activity. Some simply don’t want government agencies or even Internet Service Providers (ISPs) to know what they’re looking at online, while others have little choice. Users in countries with strict access and user laws are often prevented from accessing even public sites unless they use Tor clients and virtual private networks (VPNs). These platforms provide services related to illegal activities, such as hacking tools, malware, ransomware, or services for hire (e.g., DDoS attacks, identity theft).