Besides monitoring and improving the network, the data can be used to detect possible censorship or attacks. Due to the privacy-forward ethos of the Tor project, Tor Metrics stresses that the data it collects must not undermine the anonymity or security of the network. The dark web may be the Wild West of the internet — a place without rules, gatekeepers, or censorship — but there are still reasons to visit. Check out our list of the best dark web links and how to navigate onion and Tor sites safely. Then get a VPN to help protect your privacy on dark web websites or wherever you browse online. The Tor Browser is an open-source web browser created for anonymous browsing and to evade censorship.
FAQs On The Best Dark Web Search Engines
It’s a popular choice for users worried about online surveillance and data collection. Privacy-focused internet users who access onion sites may see greater anonymity while browsing or sharing sensitive information. These pages can also help circumvent some forms of government censorship. Technical problems also contribute to the instability of .onion links.
The Tor Times
- Tor Browser aims to make all users look the same, making it difficult for you to be fingerprinted based on your browser and device information.
- Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains.
- It has features to maximize your privacy, unlike standard web browsers that have less stringent privacy protections.
- Now that your connection is active, it’s encrypted and untraceable by your internet provider.
- Anyone can access the deep web by using specialized search engines, dedicated web directories, and other sources that can help you find the data or information.
On top of that, Tor’s nodes can also malfunction because they’re owned by volunteers, which will expose your traffic and sensitive information. This is where a VPN comes in, and a reliable VPN like NordVPN (read our NordVPN review here) can do wonders for you. We can say the same about private networks belonging to companies and other entities. Some hospitals even have classified medical records you can’t access just like that. Not Evil is a reflection of what the community is looking for and what the community reports as abusive or inappropriate content.
Understanding Onion Sites

The Dark Web is a dangerous place – You should exercise extra caution when exploring. Our search engine at GOTDW is here to help you explore more safely, but we still urge extra caution as you dive in. All content on this site is strictly for educational purposes; we neither endorse nor encourage illegal activities of any kind. Ultimately, your safety on these sites is your responsibility, so please keep your wits about you as you navigate. Navigating .onion sites requires the Tor Browser, specifically designed for privacy and accessing the dark web. Follow these straightforward steps to set up Tor and begin searching safely.
WANT TO TRY THE TOP VPN RISK FREE?
While they might sound the same, these websites are fundamentally different. The Tor browser option for streaming comes with eleven channels with varying genres. But, honestly, if you are going on the dark just to enjoy free music, we recommend that you go for free torrent platforms on the surface web instead. The wallet is free, and since it’s open-source, anyone can inspect, verify, and contribute to the code.
But online and at your finger tips, if you can make it past the surface web. Feather is a free and open source Monero wallet available on most major computer platforms. Monero is a crypto currency that can be used to conduct transactions anonymously on a peer to peer level without any centralized authority watching over.. They offer user generated reviews of forums and darknet markets, alongside breaking stories and news from the Tor-sphere. One of the most straightforward ways to access to dark web safely is via Tor, so we’ve kept that in mind when compiling our list.
Viewed from the destination, the traffic appears to originate at the Tor exit node. For most people and use cases, using only a VPN will offer sufficient privacy with much faster speeds than Tor alone. A VPN provides strong security for everyday browsing without the extra delays, middle checkpoint, and then finally the exit gate. The extra connection layers can act as a significant burden to your browsing experience if you’re doing something that is bandwidth intensive.
How To Access The Dark Web
Following these legal and ethical guidelines ensures responsible use of the dark web, protects your privacy, and helps maintain the integrity and safety of legitimate .onion resources. There are other ways for spies, hackers or other adversaries to target Tor. Lewis points to the “first contact problem”, when an attacker spots when someone moves from non-private tools to private ones, noting it’s been used to identify whistleblowers. There’s no such thing as perfectly private or secure on the internet. It’s still possible to track someone’s traffic pinging through the Tor nodes, though it is difficult.

Step-by-Step Guide: How To Access The Dark Web Using Tor Browser

It indexes a wide array of content, including both legal and illegal sites. Unlike the regular internet, the Tor network can’t be accessed via standard browsers. In Turkmenistan, one of the most isolated regimes in the world, internet censorship has evolved beyond surveillance and control. In an Orwellian twist, the people blocking access to the internet are the same ones secretly selling it back, at a price most Turkmens can’t afford.
I Found The Easiest Way To Delete Myself From The Internet – And It’s Fast

Share them in the comments below or explore more articles in our Dark Web Insights section. When you’re done surfing or shopping on the dark web, don’t forget to shut down Tails. The major advantage of using a live OS such as Tails is that, on shut down, the OS wipes itself from the thumb drive you’ve installed it.
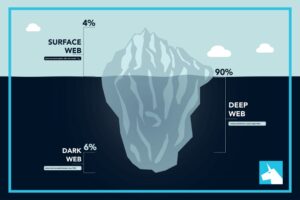
However, today’s most popular search engines — including Google, Bing, and DuckDuckGo — only index a portion of the internet. Tor websites are simply websites that can only be accessed when you’re connected to the Tor network. Instead of the more familiar top-level domains (TLD), such as .com, .org, or country-specific TLDs (like .co.uk or .fr), Tor websites use the special .onion TLD. The dark web is World Wide Web content that can only be accessed using special software, configurations, or authorization. A number of dark webs exist, including Freenet(new window) and I2P(new window), but the best known and most popular is Tor Onion Services(new window).

Find The onion Address You Want To Access
While keeping identities private is the typical case for onion sites, sometimes they aren’t concerned with their own privacy at all. For example, the New York Times and Facebook both have onion-ized versions of their normal websites to give access to people who live in places where these platforms are normally censored. Onion sites are dark web sites that can only be reached through online routing via Tor, in which encrypted data passes through multiple nodes before reaching its destination. Decrypting the data involves peeling back layer upon layer of encryption, hence the “onion” analogy. The Tor Browser is a popular online anonymity tool among political activists and journalists who fear totalitarian governments monitoring or arresting them. Other users appreciate the browser as it allows them to circumvent censorship.