
The US Naval Research Laboratory developed The Onion Routing (Tor) project in the late 90s. A network browser gives you access to sites with the ‘.onion’ registry operator. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship. The Dark Web is the part of the deep web that is not indexed by search engines, like Google or Bing.

Alternative Anonymous Networks
Human beings are fascinating creatures for a lot of reasons, in particular that for even as logical as we are, we still do some incredibly foolish or backwards things. For example, if you tell a human, “No, you cannot do that, it is not allowed,” they will find any conceivable method to do that which they are forbidden to do, even if it is utterly pointless to do so. This is especially apparent in children, but just as much so in adults. Thus, the theory goes, if you tell humans they are not allowed to purchase particular objects, or own certain items in ways they feel they are entitled to, then Hell or high water they will find a way to do it. Because it has no federated agency or nation-state backing its fiat value, nor any commodity to back it with tangible value, the trade equivalency of BTC-to-U.S. These values, though, can change dramatically for any reason and at any time.
Why Security Leaders Prefer To Buy CTI Solution For SaaS Platforms In 2025

Hence, you never know when a popular .onion site is going to vanish, or even die. Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though). The best thing is to actually understand how to find the fresh, new links. You only need to upload your PGP key or let the platform create one. Use it to link your GitHub account, Twitter, Bitcoin address, and Facebook. This .onion link makes it impossible for hackers to impersonate your profile.
More On How To Stay Safe On The Dark Web

It is one of the most active and up to date markets and always provides new and updated malware and data. Torzon Market has established itself as a significant player in the darknet ecosystem, offering a secure, user-centric platform for anonymous trading. Its commitment to privacy, diverse product offerings, and robust security measures make it a preferred choice for users seeking discreet transactions within the darknet.
How To Turn Off SafeSearch On Google, Bing, DuckDuckGo, Yahoo
- It offers outstanding privacy features and there is currently a discounted rate available through this link.
- Investing in robust cybersecurity solutions tailored to your organization’s needs is no longer optional; it is essential to ensure operational continuity and maintain stakeholder trust.
- If you’ve ever experienced an uptick in phishing attacks and spam after a data leak or breach, it may be because your personal information has been posted to the dark web.
- The concept of darknets emerged as a response to concerns about digital privacy and government surveillance.
Dark web websites are not indexed by standard search engines and can only be accessed using specialized tools, such as the Tor web browser. These sites provide a level of privacy and anonymity unavailable on the surface web, offering content and goods that cannot be easily found through traditional online platforms. To help maintain their anonymity, dark web black market users leverage a variety of tools and technologies that mask their identity and location. It’s important to know how these tools are used so you can perform reconnaissance and identify potential attacks or leaked information that can be used against you. Here is our list of 15 common technologies and tools used by cybercriminals to access and communicate via the dark web. Many users mostly rely on a dark web browser and secure Internet access to reach dark websites in that hidden part of the net.
Risks Posed To Small Businesses
Despite consistent results, this clearly leaves space for refinements. Future work may further extend the approach presented here, for example using machine learning methods to capture further behavioral regularities. Third, at any given moment we classify entities as either buyers or sellers. For example, in some cases, a seller in a given market may behave as a buyer in a second market or in the U2U network.
Personal Information
- Whether you want some pharmaceutical products (drugs) or digital items, you will probably find the products here, and that too at affordable prices.
- On the dark web, you don’t need to be a technical expert to design ransomware, and that’s dangerous.
- It is a relatively new provider but offers better features than most established VPNs.
- Proton Mail is an anonymous email service that operates an onion site.
- It uses the Tor network because it is a popular network that helps to circumvent censorship and online surveillance.
- While it hosts legitimate uses, such as protecting privacy in oppressive regimes, it is also infamous for facilitating illegal trade in drugs, weapons, counterfeit documents, and stolen corporate data.
The pre-processing relies on established state-of-the-art heuristics to cluster addresses into entities, such as cospending, intelligence-base, and behavioral clustering39,40,41,42. The resulting data set includes for each transaction the source and destination entities, the time, and the value of the transaction. The largest component of the S2S network of U2U transactions between sellers for each year with the respective number of nodes (N). The nodes are sellers that are active in that year, and an edge is placed between two sellers if at least one transaction occurs between them during that year. The network is mostly populated by U2U-only sellers, followed by market-only sellers.
Verified Social Channels And News Sites
In the vertical axis, markets are in the chronological order of their launch date, although for some markets the activity effectively starts after the launch date (e.g., AlphaBay). We use data of DWM transactions on the Bitcoin blockchain pre-processed by Chainalysis Inc. Although other coins are used, such as Monero recently, Bitcoin is still the mostly used in the ecosystem, being supported by more than 93% of markets7,9.
How To Find New, Active Dark Web Links
The key differences between dark web markets and regular online stores are clear. Regular stores are public, with visible ads and a standard payment process. They usually accept cryptocurrencies, such as Bitcoin, which keeps transactions secret. There are no visible ads or trackers, and the design is often very simple. Darren Guccione is the CEO and co-founder of Keeper Security, the world’s most popular password manager and secure digital vault.
Dark markets, as well as various other services within darknets, are hosted as ‘hidden services’. This means that the servers providing these services are only accessible via Tor and do not have a public IP address or domain name. Hidden services can operate while keeping the physical location of the server hidden, which makes tracking and shutting them down considerably more challenging. You can conduct discussions about current events anonymously on Intel Exchange.
Why Using Trusted Directories And Security Tools Is Important
It is similar to an online store, except it’s not the type you’ll find with a quick Google search. Discover everything about what a darknet market is, top marketplaces, security threats on them, and learn how to protect your data online. Freshtools is a unique marketplace in that it does not only provide the stolen data, but it allows criminals to purchase MaaS which can cause further damage to the victims.
7, we show the largest component of the S2S network one year before the operation Bayonet and one year after. The network shows a notable structural change, significantly shrinking. However, the evolution of the S2S network shows a different pattern than that observed in both the multiseller and the multibuyer networks.
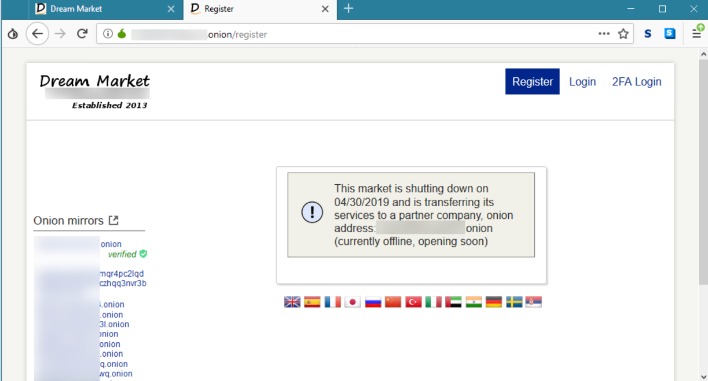
However, in April 2022, this site went offline after American and German federal government law enforcement agencies seized the website servers. Some alternative links are available, providing access to the marketplace. It’s recommended not to use new alternative links as they could just be planned exit scams. The marketplace has a pleasant, user-friendly interface built from the ground up.



