Then, simply click the operating system that you are using and download the file. The site offers downloads for macOS, Windows, Linux, and Android. While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store. That means that when Tor is compromised, or perhaps there’s a new vulnerability exploit in the Tor network, a VPN will still protect your privacy. The compromised Tor exploit might trace back to you, but then again, your VPN will lead it somewhere else – which makes it impossible to be traced back to you. But again, your ISP won’t be able to see any of the content you’re reading or what you are sending and receiving through the Tor network.

The invisible web is made up of data and information that is not indexed and cannot be searched for by using traditional search engines. It includes media and archives which cannot be crawled and indexed with current search engine technology. Finally, most privacy-savvy users fire up a VPN for the dark web before even touching Tor. A VPN can encrypt your Internet traffic and shield it from prying eyes. Suppose you connect directly to Tor without an added layer of protection.

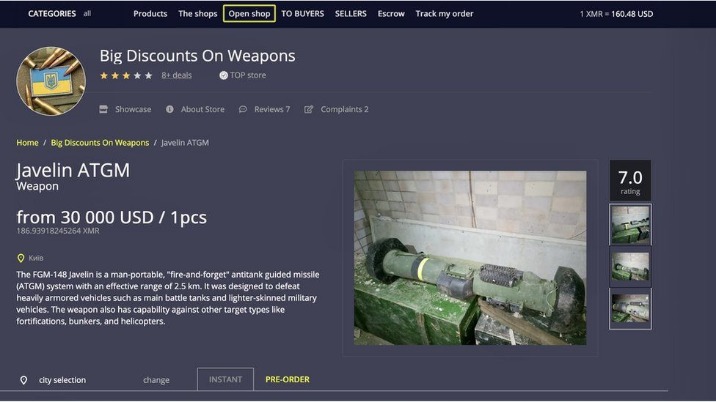
It is notorious for illegal transactions and activities such as drug trafficking, arms dealing and identity fraud. It also provides a safe haven for whistleblowers, journalists and those seeking free expression under oppressive regimes. Finding the URLs for darknet markets can be challenging, as they are constantly changing due to law enforcement actions and other factors. One way to find active darknet market URLs is to visit online forums and communities dedicated to the darknet. These communities often have up-to-date lists of active markets and can provide valuable advice and guidance for new users. Accessing any darknet marketplace is dangerous because it is known to be a hub for illegal trade.
Shaping The Future Of Torzon Darknet
To remain anonymous about your purchases on the dark web, always use cryptocurrency as your mode of payment. If a seller encourages you to opt for other well-known and commonly used payment methods, then the person is likely to be a scammer, and you must not make any deal with them. The website has a sleek design and interactive user interface, making it the most preferred choice in terms of user experience. You can pay through Monera and Bitcoin using the escrow system or the traditional market account after making a purchase on this shop. Since the dark web can be accessed through the Tor browser, use a VPN with the Tor browser to ensure increased protection.
Cybercrime Increasingly Moving Beyond Financial Gains
Be sure to use a strong, unique password and consider using a VPN to further protect your privacy. If you’d like to use it to exchange currencies, please feel free. To access the darknet you’ll need to download and install the Tor (the onion routing) browser. Many users mostly rely on a dark web browser and secure Internet access to reach dark websites in that hidden part of the net.
Also, these aren’t auto-updated as is the case with search-engines. Hence, you may find more dead links on link directories than on search-engines. AES encryption is used, arguably “the” strongest encryption on the planet.
Darknet Websites Uncovered

It operates in both French and English and has built a reputation for ease-of-use. Known for its publicity stunt releasing millions of stolen card details for free, BidenCash specializes in credit card fraud and identity theft. It is one of the most controversial platforms, active since 2022.

Creating A Tor Account

Then, use data breach monitoring software to help find out if your personal data has leaked onto the dark web. While accessing Darknet Markets themselves is typically not against the law in most places, engaging with illicit goods within them is generally considered a crime. On the other hand, some people might visit Darknet Markets for lawful purposes such as research, journalistic work, or simply to explore online communities. It’s essential to know the local laws regarding online activities, and be cautious when using these platforms to avoid any potential issues. Meanwhile, cybersecurity experts monitor the dark web, scanning for stolen data and emerging threats. If your information surfaces in these murky depths, there’s very little you can do – but knowing the risks involved is a first step toward defence.
Protect Your Personal Data
Dark web commerce sites have the same features as any e-retail operation, including ratings/reviews, shopping carts and forums, but there are important differences. When both buyers and sellers are anonymous, the credibility of any ratings system is dubious. Step into the world of Archetyp, where anonymity reigns supreme. Archetyp Market is an online darknet marketplace, founded in late 2021. If your IP can’t be connected to you, you can’t be held responsible for any of your actions.
Where Torzon Url Enthusiasts Unite
Keeper has millions of consumer customers and the business solution protects thousands of organizations worldwide. All this activity, this vision of a bustling marketplace, might make you think that navigating the dark web is easy. The place is as messy and chaotic as you would expect when everyone is anonymous, and a substantial minority are out to scam others. Medical records, fee-based content, membership websites, and confidential corporate web pages are just a few examples of what makes up the deep web. Estimates place the size of the deep web at between 96% and 99% of the internet. Only a tiny portion of the internet is accessible through a standard web browser—generally known as the “clear web”.
The first step is to download and configure the Tor browser from its official website. The Tor browser is your gateway to the dark web, allowing you to access .onion sites anonymously. Immerse yourself in a world of endless inspiration with torzon url. From stunning torzon darknet creations to insightful tutorials, our platform offers a wealth of resources to fuel your passion for torzon mirror and take your skills to new heights.
These search engines neither track your search queries nor record any information, improving digital privacy and keeping your data private. Don’t ever reveal your true identity on the dark web marketplaces because there’s a high chance of hackers and scammers misusing it. Beware of sharing your financial details on the dark web, as this can result in identity theft and your bank account amount being stolen. The Silk Road was a famous dark web marketplace where users could buy and sell goods and services anonymously.
- Try using tools like password managers like Keeper, Passbolt, 1Password or others.
- Imagine trusting a site where you’ve been buying or selling for months, and everything seems legit.
- These hackers don’t hide in the shadows as much as you might think.
- There are currently several online darknet markets, but they tend to be incredibly volatile due to government intervention.
- The name of this dark web browser comes from the method it uses to encrypt messages.
By using Tor and a reputable VPN, along with being careful and having the right tools, you can browse the dark web legally and safely. Responsible use protects your privacy while staying within the law, so it’s a safe place to browse for real privacy reasons. Typically, you can find dark web URLs through forums, databases, or by talking to others who frequent those sites. Dark web forums typically look like run-of-the-mill message boards. The real difference lies in what you can post and the poster’s anonymity.
These listings often include detailed descriptions, user reviews, and even shipping guarantees. Even if you’ve never visited these markets, your personal and financial data might already be there, having been leaked through a data breach. Criminals use this information for money laundering, opening bank accounts, applying for loans, and draining your finances. A Canadian market established in 2021, WTN offers over 9,000 products, including narcotics, fake goods, and digital services.
By encrypting communication before it gets to the Tor network, pairing Tor with a VPN gives a second degree of protection. By distributing communication over several nodes, it obscures the user’s IP address. Research of the dark web is legal as long as national or international laws are not broken. However, it’s very difficult and would require extensive resources, meaning that the average person’s identity is unlikely to be uncovered. Before entering the dark web, you need to download a dark web browser—most people use Tor (The Onion Router) or I2P (The Invisible Internet Project).



