The search engine doesn’t impose censorship, meaning you can find a broad spectrum of sites, including those that may be illegal or disturbing. OnionLand offers a clean design with a simple user interface that includes search suggestions. The search engine allows you to look for old V2 onion addresses, images, and content on I2P. It also conducts searches across both the clearnet and dark web by leveraging multiple indices, so you can filter searches to focus exclusively on the darknet or span both realms.

All this activity, this vision of a bustling marketplace, might make you think that navigating the dark web is easy. The place is as messy and chaotic as you would expect when everyone is anonymous, and a substantial minority are out to scam others. There are also many tools that can be use to monitor the dark web and scan for personally identifiable information and even respond to attacks.
- While Tor provides strong anonymity, activity can potentially be traced through advanced techniques like timing attacks, exit node monitoring, or vulnerabilities in engine setups.
- Use categorized directories or reputable search engines to reduce the chance of clicking on spam or malicious links.
- It was created by “Tim Berners-Lee”, who was also the creator of HTML and the Web itself.
- It works by routing your encrypted traffic through multiple volunteer-operated servers, known as onion routers.
- I2P, or the Invisible Internet Project, is an anonymous network layer to facilitate secure and private communication among its users.
Separate Your Real Life From Your Online Persona
It is essentially a list of all the notable websites available on the Tor Network that is kept in a single, organized place. The Tor network is designed to provide you with privacy and anonymity. That said, most experts agree that at least some nodes on the Tor network have been compromised by intelligence agencies like the CIA and the NSA. This design choice significantly reduces the risk of inadvertently clicking on harmful links or dangerous sites. The Not Evil is relatively safe, as it doesn’t track users; however, it doesn’t filter malicious content, so caution is still needed. Although reported as active, there is limited information on Not Evil’s current status, so availability may vary.
Top Dark Web Search Engines In 2023
Users must manually scroll through categories, many of which include outdated or broken links. Because it doesn’t use a crawler or ranking algorithm, OnionLinks is static and highly dependent on manual submissions, which makes it unreliable for current or time-sensitive research. The dark web is bottomless and continues to grow each day, and so does the number of tools used to get around in it. Here’s a breakdown of the most commonly used dark web search engines in 2025. The basic architecture of a standard web crawler, such as those used by Google, relies on indexing from seed URLs, analyzing metadata, and following link structures.
Understanding Risks And Staying Safe On The Dark Web

So, you should also make sure that your system’s operating system and other installed software are patched with the latest updates. However, we strongly advise against using dark web marketplaces due to legal risks and the high likelihood of being scammed. What’s more, they can also sell you personal information on the dark web as your personal data has a monetary value on the dark web. You can check our guide on the best VPN services to find the right VPN solution to protect your privacy. You can use these dark web investigation tools to check if your company’s data is available on the dark web.
Use A VPN

Standard web browsers like Chrome or Firefox won’t suffice to access the dark web. Specialized dark web browsers provide the necessary layers of encryption and anonymity. To safely access the Dark Web, download the Tor Browser, which anonymizes your internet connection. For added security, consider using a VPN like Forest VPN to further encrypt your data and maintain your privacy. Perhaps the best-known thing you can buy on the Dark Web is information collected in what seems like the almost daily data breaches we read about in the news.
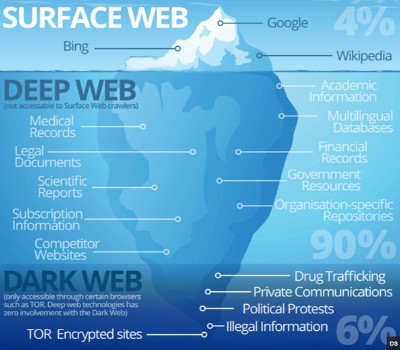
Learn The Difference Between Dark Web & Deep Web
If you are in a position to report the incident safely, you should report it to the authorities immediately. It’s recommended not to be too vigilant here and leave the investigation to the professionals. Some services are genuine; you can get what you want at an agreed fee.
While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store. So, once you’ve activated your VPN and your privacy is secured, it’s time to visit Tor’s official download page. Make sure that when you download the Tor file, it’s from their official website. It’s impossible to access the dark web with a regular browser like Chrome or Safari. As you are now familiar with the three different sections within the entire world wide web, let’s take a closer look at how you can access the dark web anonymously. We’ve also previously mentioned the “dark users” that use the dark web for illegal reasons, but the less said about them, the better.
How Dark Web Search Engines Work
Cryptocurrency miners and other malicious software often target dark web users. Using a reliable antivirus to scan your device is worthwhile if you spot suspicious spikes in system resource usage. Set Tor Browser’s security level to “Safest” for critical dark web activity.
- Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools.
- Using a VPN alongside Tor adds an extra layer of security by hiding your IP address from Tor entry nodes and encrypting your traffic.
- The lack of standardization and numerous malicious sites further complicate navigation.
- There are multiple search engines on the dark web that can help you find what you’re looking for.
Operating on a freemium model, users have the option to upgrade for an ad-free experience and access to features like historical website versions. Similar to DuckDuckGo, Haystack prioritizes user privacy, pledging not to track data or compromise privacy for profit. Navigating the dark web presents challenges; its links are lengthy, and its sites are generally obscure. To explore the dark web, one must first utilize a dark web search engine.
The Haystak search engine does not track your data or compromise your privacy, although the free version will serve you occasional ads. The dark web is a part of the internet that isn’t indexed by search engines. You’ve no doubt heard talk of the “dark web” as a hotbed of criminal activity — and it is.
When searching the darknet, OSE’s informative search page proves invaluable. It not only displays websites but also indicates whether the URL is currently online or offline—a crucial feature given the transient nature of .onion domains. Additionally, OSE provides the “last update” date for each URL, enhancing user transparency and trust. To access Recon Dark Web Search Engine, users must utilize the Tor browser, specifically designed to connect to hidden websites on the Dark Web.
With an index boasting over 100,000 web pages, including various Dark Web marketplaces and forums, Candle caters to users seeking diverse content within the hidden corners of the internet. Users play a crucial role in shaping the platform, reporting abusive or inappropriate content to ensure a safe and relevant browsing experience. While not Evil does not claim divine authority, it relies on user feedback to identify and address problematic links or hosts. DuckDuckGo doesn’t log your activity, so your search habits, dark web or not, remain private to you.
As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web. There are often copious amounts of how-to articles, software exploits, and hacked credentials for sale. Not every visitor is a criminal, but this is where most cybercrimes begin.