When you install the Tor Browser, it comes preconfigured with the most secure privacy settings. That means Javascript is disabled, extensions are disabled, and the browser is configured to warn you if an attempt is made to download a file and open it in another application. Trying NordVPN is risk-free, given its 30-day money-back guarantee. I tested out their refund process and was pleasantly surprised by the speed and ease of the transaction. After a brief conversation with their support, my refund was processed within minutes, and I saw the funds in my account within a week.
There’s a significant risk to dark web users of being exposed to malware (malicious software) infections. There are several programs that hackers frequently use on the dark web. On top of that, the installation process of Freenet is rather easy. Simply download the file, install the software, and you’re ready to use its web-based interface.
Proton Mail
ExpressVPN is a top-rated free VPN trial for the Dark Web, offering unlimited bandwidth, 3,000+ servers in 90+ countries, and high-end privacy and security. Depending on your activity, it can be okay to look at the dark web, but we recommend using extreme caution and researching exactly where you want to go before you start clicking around. While many people use it for legitimate purposes, the dark web also hosts illegal activities that you don’t want to stumble upon or engage with.
Tor-Enabled OS Alternatives To Tails For Secure Dark Web Browsing
It’s also a fantastic torrenting VPN, primarily because all of its servers are P2P-optimized, unlike most of the competition. The best VPN for beginners doesn’t scrimp on performance, either, reaching peak speeds of over 750 Mbps in my latest tests. That’s fast enough for everything, including torrenting, gaming, streaming, and more.

What Are The Dangers Of Accessing The Dark Web?
This guide reviews tools such as Tor, I2P, Whonix, and more for accessing the hidden web securely. With over 15 years of experience in content creation and digital publishing, he knows how to craft informative, useful content, with thorough research and fact-checking to back it up. He strives to make complex cybersecurity topics accessible and understandable to the broadest audiences. In his spare time, Michael likes writing fiction, reading murder mystery novels, and spending time with his family.
Table Of Contents
Further below we’ve also analyzed two 100% free Tor VPNs, although they underperformed top-rated services. They will enhance your internet privacy when browsing the Dark Web, particularly using the Onion over VPN method of combining the two technologies. When used correctly, these VPNs will hide your IP address from Tor’s entry nodes and allow you to use Tor more safely. We’re fully independent and have been reviewing VPNs since 2016. Our ratings are based on our own testing results and are unaffected by financial incentives. They also need to work seamlessly with the Tor Browser and the Dark Web, and shouldn’t collect any identifying activity logs.
Can You Use The Tor Browser On A Mobile Device?
This TrustedServer setup has even been put to the test when the Turkish government seized a server, but couldn’t recover a thing. Since the dark web is full of many inherent dangers, sometimes you need more than a VPN to protect you. If you’re new to the dark web, check out our beginner’s guide on how to stay safe while browsing Tor. Microsoft Word is one of the best word processors around, allowing you to craft powerful documents with an intuitive interface. If you know how to use Microsoft Word, you’re typically working with large files that span multiple pages.
Notes From The Lab: Proton VPN Speed Test Results

Using this method is as simple as connecting to a VPN, then connecting to Tor. You can also test Surfshark risk-free with its 30-day money-back guarantee. If you’re not happy with the VPN, you can easily get a refund; just use the 24/7 live chat feature, like I did. Perhaps the best-known thing you can buy on the Dark Web is information collected in what seems like the almost daily data breaches we read about in the news. That information can include checking and credit card account numbers, social security numbers, and other sensitive information.
- Finally, ProtonVPN has a verified no-logging policy and is open-source, meaning you’re extra safe from anyone or anything demanding your logs.
- However, if you maintain your anonymity to the best of your ability and always use your VPN, you’re unlikely to be tracked.
- It’s also a fantastic torrenting VPN, primarily because all of its servers are P2P-optimized, unlike most of the competition.
- With rising curiosity around hidden corners of the internet, many professionals wonder, “how to access the dark web” safely.
- ExpressVPN works well with Tor, Freenet, and Invisible Internet Project (I2P).
Arguably the most important feature to look for is the VPN’s data logging policy. Ideally, the VPN should have a strict no-logs policy and be based in a privacy-friendly country. That way, you don’t have to worry about your data falling into the government’s hands or getting stolen by any malicious third party. For added security, use a separate device or virtual machine (VM) when accessing the dark web. A VM can act as a protective barrier between your main device and any potential threats.
Once you’ve opened the browser and you’re connected to the Tor network, that’s it. All you have to do is find an Onion URL (it’ll end in .onion) you want to connect to, and enter it into your browser. If you’re using a VPN like NordVPN that gives you direct access to the Onion network, you can skip this step and use any browser. It’s a little more expensive than its competitors without bringing much more to the table unless you’re using it from a jurisdiction with highly restricted internet access.
Is It Safe To Access The Dark Web With A Free VPN?

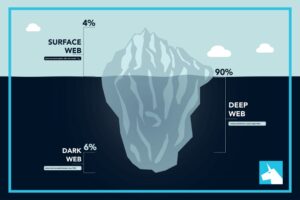
That means that only 0.024% of all the known pages are findable in Google’s search engine. The users only have access to a fraction of the available data and web pages. Avira Phantom VPN has a decent free plan with a simple interface, only 1 server option, up to 1 GB of data per month, and decent security (though no kill switch).

In the meantime, the provider does operate a verified no-logging policy – so at least your dark web life will stay private if the authorities demand your logs. The VPN provider also used to offer a .onion address, but since the update from v2 onion to v3, it appears to be defunct. In second place is ExpressVPN, thanks to its lightning-fast speeds and automatic obfuscation on every VPN server with any protocol. Anyway, NordVPN is also equipped with premium security features.
Once you upload something, it stays there indefinitely even if you stop using Freenet, so long as it is popular. A VPN allows a user to encrypt all internet traffic traveling to and from his or her device and route it through a server in a location of that user’s choosing. A VPN, in combination with Tor, further enhances the user’s security and anonymity. Dark net websites are called “Tor hidden services”, and they can be distinguished from normal websites by their URLs. Tor is a network of volunteer relays through which the user’s internet connection is routed. The connection is encrypted, and all the traffic bounces between relays worldwide, making the user anonymous.
DuckDuckGo is the best dark web search engine, as it offers an excellent user experience akin to surface web search engines. Its effectiveness in scouring the shadowy depths of the dark web can be likened to what Google does on the surface web. There’s evidence that law enforcement agencies in freer countries operate many exit nodes for monitoring and surveillance purposes.