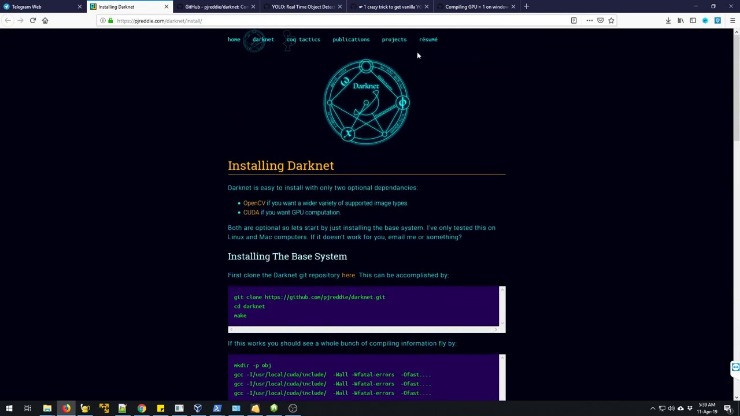
For a number of technical reasons, it’s much faster and more reliable than Tor. The peer-to-peer routing structure is more advanced, and it does not rely on a trusted directory to get route information. I2P uses one-way tunnels, so an eavesdropper can only capture outbound or inbound traffic, not both. The big downside is that your ISP will know you are using Tor, which is cause for concern in some places and will put many people off using this method. In this instance, too, it is important to use a logless VPN and pay with Bitcoin if you can to stay anonymous. The VPN over Tor technique is also susceptible to an end-to-end timing attack, though it’s highly unlikely.

Q2: Will My VPN Protect Me On The Darknet?
It is often used for illegal activities such as buying and selling drugs, weapons, and stolen data. However, it also has legitimate uses, such as providing a platform for free speech, whistleblowing, and journalism. The darknet is a part of the internet that is not indexed by traditional search engines, and it requires specific software to access.
Bonus Tip: How To Spoof Or Change Your GPS Location On Your Mobile Device? Check Below:
Any fraud can buy stolen IDs and passwords to your online banking or launder money. On some resources, black transplantologists can get orders for human organs and kidnappers or traffickers can discuss their next victim. It is a small part of the Deep Web and includes all overlay networks, which use the Internet for their work but are accessible only through special software and tools.

Minimize Or Rescale Your Tor Browsing Window
- This allows you to use the computer without the risk of corrupting your computer’s normal operating system with viruses or malware.
- For instance, the website of the Torch dark web browser is cnkj6nippubgycuj.onion, while the Tor website for DuckDuckGo is 3g2upl4pq6kufc4m.onion.
- It’s worth mentioning that neither of these VPN providers are known for their high speeds, so you may experience some lag when browsing the dark web on your Android device.
- These websites are categorized as search engines, publication sites, email services, cryptocurrency sites, and miscellaneous sites.
- However, accessing the darknet on Android devices can be challenging for many users.
These websites are often used for illegal activities such as drug trafficking, weapons sales, and child pornography. However, there are also many legitimate uses for the darknet, such as protecting political dissidents, whistleblowers, and journalists from government surveillance. By approaching the Dark Web with knowledge, understanding, and caution, you can safely explore this hidden realm on your Android device. Enjoy the journey, but always prioritize your safety, privacy, and adherence to the law. In the next step, we will explore how to navigate the Dark Web and ensure your safety while exploring this hidden realm on your Android device.
How To Sell Counter-Strike 2 Skins Instantly? A Comprehensive Guide
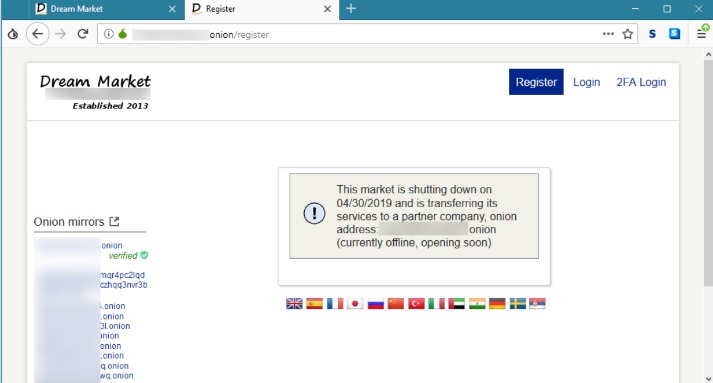
Cryptocurrencies, such as Bitcoin, are preferred on the dark web due to their ability to offer anonymity and decentralization, which are not available with traditional forms of currency. Although transactions made with cryptocurrencies are recorded on a public ledger called the blockchain, the identity of the sender and receiver remains undisclosed. Transactions are linked with a public key, which is a distinctive identifier that does not disclose personal information. Within the Tor Browser, navigate to the security settings and adjust them to the “Safest” level. Please check your local laws to ensure your use of VPN complies with statutory requirements. If you’re planning to return, consider creating a burner OS or using a hardened Linux distro like Tails.

Step 1: Choose A Security-Focused Android Browser
- The deep web contains sites and pages that are often prevented from being indexed by search engines and contain unlinked content.
- Then, simply click the operating system that you are using and download the file.
- In recent years, the darknet has gained a reputation as a haven for criminal activity, but it also has legitimate uses for those who value their privacy and security.
- Also, the bad actors can use tools like keyloggers to gather data and infiltrate your system.
However, it is important to note that engaging in illegal activities while browsing the Dark Web is a criminal offense and can lead to severe legal consequences. The dark web is content that exists on dark nets, which require specialized software (like the Tor Browser), configurations and authorization to access. These can include the previously mentioned illegal offerings, but can also include ultra-private information designed to be shared only with certain parties. Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails. This includes evidence of any websites you visit, files you open, passwords you use, and even any other devices or networks you connect to. Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down.
How To Access The Dark Web On Android
But human trafficking, illegal pornography featuring underaged victims, money laundering, and assassinations are also examples of the darkest corners on the dark web. The majority of the web is called the “deep web” (often referred to as the “invisible” or “hidden” web). The deep web is basically all the content that you can’t find using Google or Yahoo search. So, that means that the number of pages increased by over 100 trillion in just over three years. Hypothetically speaking, Google may be aware of well over 200 trillion individual pages (these are obviously NOT all indexed in the search engine).
Change Your Browsing Habits
Anyone can access the dark web, and it’s not that complicated to do so. The advantage of using a dedicated computer just to browse the dark web is that your main computer isn’t exposed to any of the threats or risks tied to entering the dark web. In case of an attack, you can be sure that any of the data or information stored on your main computer will be safe. Opennet connections are easier to use, but darknet connections provide more security against attackers on the network. In darknet mode, you can select friends on the network and only connect and share dark web content with them. This enables individuals to form groups and only share content in a highly anonymous network of darknet users who they know.
For those looking to explore this hidden part of the web using their Android devices, it’s essential to understand what this entails and how to do it safely. In recent years, the darknet has gained significant attention due to its association with illicit activities. This article will provide a comprehensive guide on how to access the darknet on Android devices. The darknet is a collection of websites that are not indexed by search engines and are only accessible through specialized software. These websites use the Tor network to provide anonymity to their users.

Is It Safe To Access The Darknet On My Phone?
Finally, continuously verify every Onion site you visit using dark web Wiki guides. Hopefully, this advice about browsing the dark web on an android or other device has answered some of your questions. The Dark Web is one of the most misinterpreted expressions, with individuals exaggerating what is a simple concept. You must realize that the dark web is a component of the internet that is not indexed as you discover how to access it on your phone. This method assumes that you have either Google Play or F-Droid installed on your mobile device.
It’s important to note that not everything in this space is illicit; it serves as a refuge for privacy-conscious individuals and whistleblowers. The darknet is a part of the internet that is not indexed by traditional search engines. It requires specific software for access, providing anonymity to its users.
This allows you to use the computer without the risk of corrupting your computer’s normal operating system with viruses or malware. Tails is a mere 1.3 GB download, so on most connections it will download quickly. While this is good advice for any type of web browsing, be particularly careful not to offer up any personal details, such as your credit card info or email address. Use cryptocurrency to buy anything, and use a disposable email address for any type of communication on the dark web.
The VPN encryption will prevent snooping eyes from seeing the Tor entry nodes that can’t see your IP address and hide Tor activity from your ISP. Accessing the dark web through your phone is much more dangerous than accessing it through a desktop or laptop, primarily because cell phones are personal diaries. They have several bits of personally identifiable information such as usernames, bank details, social security numbers, and even your location. If that information ends up in the wrong hands, it could make you a victim of harmful things such as identity theft.
Many experts advise against using third-party mobile browsers that utilize the Tor Network. If you come across suspicious links, you should avoid clicking on them. It’s important to verify the legitimacy of a website before interacting to protect your personal data and security.



