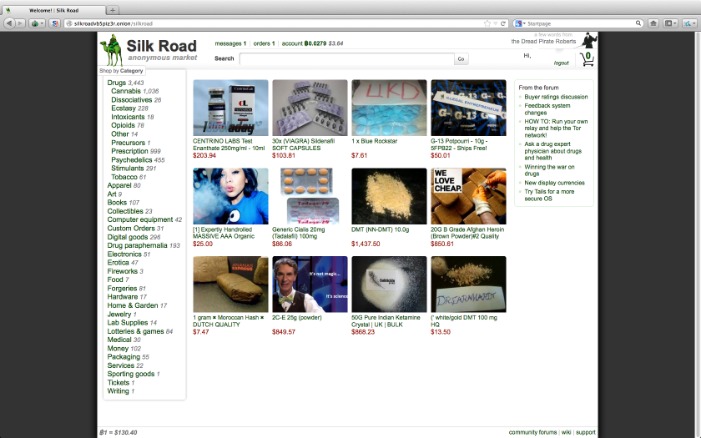
The marketplace has several rules that every user is bound to follow. If any user is found not complying with the law, strict and immediate action will be taken against them. It uses PGP encryption to protect sensitive data and messages, and accepts payments via Monera and Bitcoins to keep you anonymous on this marketplace.
Official PGP Key
We will be exploring the top 10 Dark Web markets in this article. From items like drugs, fake ID cards, and hacked bank accounts to more complex offerings like human trafficking, these sites carry all the illegal activities you can think of. The dark net is famous for being a hub of black market websites for buying and selling products and services. Using a dark web search engine is a great step towards enjoying a more secure experience while shopping on the platform. Not all marketplaces you want to visit can be accessed through regular search engines. In addition, mainstream search engines also track your searches and collect personal information.
Law enforcement agencies monitor many dangerous markets, and even anonymous browsing isn’t foolproof. Just visiting these sites can attract attention from law enforcement, especially if you interact with known vendors or download suspicious content. The fallout for victims whose data is stolen and sold can be devastating.

VPN Alternatives For Securing Remote Network Access

Furthermore, inexperienced users unfamiliar with secure cryptocurrency practices are particularly susceptible to these threats, risking the loss of their entire funds. Users must look for platforms employing robust encryption protocols, secure escrow services, and advanced anti-phishing measures. Additional layers, such as two-factor authentication (2FA), encrypted PGP messaging, and built-in wallet security, significantly enhance protection against theft and hacking. Significant technological innovations and trends have reshaped dark-web marketplaces over recent years. In 2025, many platforms have adopted decentralized architectures, reducing single points of failure that previously made them vulnerable to law enforcement takedowns.
Illicit And Risky Use-Cases
If the main DarkMatter onion URL is unavailable, please attempt one of the verified mirror links provided on this page. 7 monitored transactions with buyer feedback during a 21-day evaluation on the DarkMatter onion platform. Established in 2022, WizardShop is one of the biggest data stores on the dark web, focusing mainly on carding and financial data. STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity.
The only way to access the dark web is by using the correct browser and knowing the URLs of the pages you want to visit. Scroll on to learn more about dark web links (also called Tor links or onion sites), get the right links for some of the best Tor sites, and find out how to visit them safely. Blockchain even has an HTTPS security certificate for even better protection.

Report It To The Authorities (if It’s Safe To Do So)
Over time, ambitious individuals created infrastructure for these transactions, where for a fee, sellers have access to a digital ‘storefront’ to sell their products in a centralized marketplace. Given the darknet’s infrastructure, which is hidden behind onion routing, the darknet attracts sites whose proprietors want to remain anonymous. Beginning in September 2021, Abacus Market has established itself as one of the leading dark web marketplaces. After AlphaBay closed, Abacus Market took its place as the world’s largest underground darknet marketplaces. Abacus Market quickly rose to prominence by attracting former AlphaBay users and providing a comprehensive platform for a wide range of illicit activities. Most buyers and sellers use the Tor network, which hides IP addresses and locations.

The Emergence Of Marketplaces On The Darknet
You risk being targeted for attacks if you explore the dark web without protection. The threat can extend to your entire network of devices connected to the internet. Law enforcers can use custom software to infiltrate the dark web and analyze activities. You could be monitored closely even if you are not doing anything illegal. The use of the dark web raises suspicion as it shows there is something you want to do privately.
Keep Your Identity Hidden

The system is designed to provide enhanced security and privacy features. Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity. The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address. Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved. No user names are tied to actual identities, and no moderation like one may find on Reddit. Users leverage these platforms to organize protests, whistleblow, share survival guides, or share files P2P.
Established in 2012, the platform is a time capsule that collects snapshots of websites. These onion addresses will remain online even if the original page disappears. It also keeps the graphical copy and text of the page for better accuracy. Using the ProtonMail .onion site offers security and privacy advantages.
Accepting BTC, XMR, and LTC, it caters to a broad audience with its low transaction fees (as low as 3%). Drughub’s unique access system includes rotating mirrors to combat DDoS attacks, ensuring 99.4% uptime. With a growing vendor base and responsive 24/7 support, it’s a solid pick for users seeking niche products and reliable service in 2025.
- When he’s not empowering PrivacySavvy’s readers to take control of their online security, Saheed enjoys distance running, playing chess, and exploring the latest open-source software advancements.
- You can also use it within the dark web, as it has .onion links.
- FreshTools, founded in 2019, specializes in selling stolen account credentials and data, particularly webmail, RDPs (Remote Desktop Protocols), and cPanels.
- It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products.
- For instance, you can choose the preferred security levels for enhanced protection.
- Unlike many other dark web markets, Cypher does not require buyers to deposit cryptocurrency upfront, which reduces the risk of exit scams.
Is Accessing The Dark Web Illegal?
A reliable, fast, and user-friendly VPN service offering lots of customizable options for privacy geeks. ActiveX and Java frameworks are susceptible to being exploited by hackers. Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe. In some countries, evading government restrictions to seek new political ideologies is punishable. For example, China uses the Great Firewall to block access to Western sites. Accessing blocked content can result in being placed on a watch list or imprisonment.
Criminals use this information for money laundering, opening bank accounts, applying for loans, and draining your finances. Dark web markets work much like regular e-commerce websites but with extra layers of anonymity and encryption. Buyers browse listings, place orders, and pay with cryptocurrency — typically Bitcoin or Monero — to obscure transaction trails. They sell these files for just a fraction of the original cost on the surface web or even share freely, which makes them tempting for people looking for shortcuts.
It’s similar to Reddit or Quora but designed for anonymous users. Users can ask questions, share answers, and engage in discussions without revealing their identities. It’s maintained by a volunteer-run collective from the USA that protects the platform from malicious attacks and pledges to support social justice and progressive causes. Riseup’s secure email and chat help individuals communicate without fear of surveillance or data interception. Accessing ProPublica via the Tor Browser gives users an added layer of privacy and lets them bypass restrictive government censorship.



