
Outdated software can have vulnerabilities that may put you at risk. Files on the dark web may contain malware, and it’s best to avoid downloading from unknown sources. Since .onion URLs can be complex and random, consider bookmarking reliable sites in Tor for easier access.
Do I Need A VPN If I Access The Dark Web On My Phone?
These corners are deliberately concealed from the public eye and require specialized tools and browsers to access, making it more difficult for the average person to explore. The dark web is not meant for the general public since it is harder to access and need technical knowledge. However, some activities on the dark web — such as illegal marketplaces or hacking forums — can be against laws in many jurisdictions.
Is It Illegal To Access The Dark Web?
While there are other options, these are the only browsers officially recommended by the Tor Project. Using a different browser than these could put your privacy at serious risk and could expose you to attacks from cybercriminals. Tails is an open-source Linux-based OS that never writes to the hard drive or SSD. This feature ensures that the programs baked into the OS don’t leave a digital footprint on your machine. Think of it as a whole separate operating system, complete with apps and files, that runs entirely on removable media. When you’re done, clear your browsing history, power down your machine, and ensure no traces of your session remain.
Tips For Accessing The Dark Web
Fortunately, it’s not a criminal offense if you simply search the dark web, but if you use it to carry out illegal activities, you get in trouble. This can lead to incrimination for other activities later in life. China, for example, uses the “Great Firewall” to restrict access to popular sites and prevent citizens from evading government restrictions. The dark web is a hidden part of the internet that can be accessed through limited resources. Moreover, you need to be more cautious while accessing it, as without proper safety, you can fall into the wrong hands and face serious consequences.
The deep web is basically all the content that you can’t find using Google or Yahoo search. So, sites that contain a domain extension like .com, .org, .net, .biz, .info, etc. can be found on the surface web. In addition, the content on the pages don’t need any special or custom configuration to access. Did you know that Google only shows you a glimpse of all the websites that actually exist? The last time I checked, it’s estimated that the entire web is roughly 500 times larger than what Google returns in Google Search.
How Can I Differentiate Legitimate Services From Scams On The Dark Web?
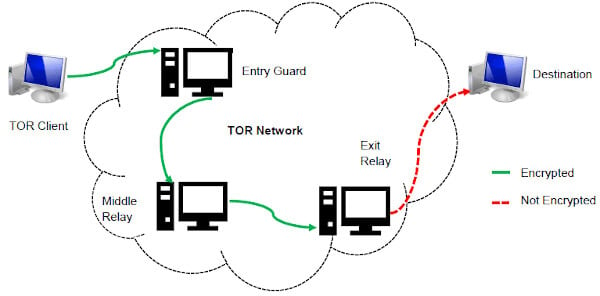
Freelancing alongside these roles, his work has appeared in publications such as Vice, Metro, Tablet and New Internationalist, as well as The Week’s online edition. In this way, your browsing experience is made as anonymous as possible – if someone was ‘watching’ you, so to speak, all they’d be able to see is that you’re using Tor. For information about this, check out our guide on how to get on the dark web. To access the Dark Web, you have to use a browser called Tor, also known as The Onion Router. This is the only way to ensure a maximally anonymous – as well as safe – browsing experience on the Dark Web. With dangers like this in mind, it’s even more important to stay safe when surfing the Dark Web than any other part of the internet.
However, data is required for understanding, monitoring, and improving the network. Furthermore, data will help to detect attacks against the network and possible censorship events. Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal. Facebook’s dark web version allows users to access the site where it is banned or restricted. Although the social application is known for collecting data on its platform, it does not like sharing the information with others.
Be sure to configure both your VPN and browser to block these leaks. Popular VPNs like ExpressVPN and NordVPN come with built-in leak protection. Go to the Google Play Store and download the official Tor browser. David is a programmer and writer who has worked as a software developer at MIT.
Here are all the quick security tips to securely get on the dark web. This is why I strongly advise anyone visiting the dark web to exercise the greatest of caution during their dark online travels. Check out my article for more information about the dark web and how to access it while staying safe. One way to stay safe is to use a VPN while accessing the dark web, so be sure to check out my article on the best VPNs for the dark web.
- Surfshark is a low-cost provider that ticks all the boxes for use with the dark web.
- VPNs are often recommended as protection in such cases, but Whited disagrees.
- As a result, you should avoid opening unfiltered sources, torrent sites, and dark web links unnecessarily and downloading every file you come across.
- After connecting to the Tor network, the Brave browser in the bottom left corner, “If your personal security depends on staying anonymous, use Tor Browser instead.” gives a warning.
Is The Tor Browser Safe Without A VPN?

Outside of work, she is a travel enthusiast, music lover and avid learner interested in global cultures, spirituality, psychology and neuroscience. With your VPN up and running and all of your other apps closed down, you’re finally on the brink of actually accessing the dark web. To access the surface web or the deep web, all you need is a standard internet browser like Google Chrome or Safari. For the dark web, though, you need an entirely different entry point known as an overlay network.
Finding And Accessing Sites On The Dark Web
Indeed, we follow strict guidelines that ensure our editorial content is never influenced by advertisers. It offers outstanding privacy features and is currently available with three months extra free. The dark web is hard to stop because it’s difficult to track and monitor activity since much of it is encrypted. Plus, controlling access to the dark web would be a massive undertaking. For its part, Mullvad says that it would “cease operation of our service” if forced by legal means to spy on users. Internet traffic is protected using 256-bit AES encryption, together with a SHA384 hash and 4096-bit RSA keys for OpenVPN and IKEv2.
Onion Links: How To Access Them
The Safer level enhances security by disabling certain features, and the Safest level entirely blocks scripts, which may impact some functionality. Once connected, you should be redirected to the browser’s homepage. But, to get there, you need a special kind of browser because the Dark Web is all about keeping things under wraps with encryption. If you want to dive into the Dark Web using your smartphone, I’m here to debunk the myths and walk you through it step by step. Ready to start your undercover internet adventure on your Android or iPhone? Join millions of users who trust ForestVPN for privacy and unrestricted internet access.
How To Get The Tor Browser
Several pedophile chat sites were also dismantled, and four people were detained, one of them a Paraguayan suspected of running the network. The most prevalent dark web content is child pornography, about 80% of its web traffic, despite being challenging to find. Other porn-related content found on the dark web includes revenge porn and sexualized torture, and the killing of animals.

There are numerous directories that host .onion links and websites, but you should always exercise caution. That said, it’s worth noting that the Tor browser is not the same as a VPN. It connects you to a network of servers rather than a particular server.

What’s more, it’s a network that includes assassins for hire, child pornography, and even live streams of murders. If you accidentally end up on one of those pages, you may face legal charges should someone find out. To prevent these types of dangers, I recommend browsing the dark web with a direct goal in mind — research specific sites ahead of time and keep a list of links that you can trust. Browsing the dark web puts you at risk of cyberattacks such as DDoS attacks, botnets, and other malware or viruses. By simply entering the wrong URL or accidentally downloading a malicious file, you could install infectious viruses or malware.



