Tor has an in-build slider which lets you adjust the level of security. This means that the JavaScript will be disabled by default on every website and some symbols and images will not be displayed. In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web. At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen. Well, VPN over Tor is basically its opposite – instead of going through the VPN first, the signal passes through the Tor network, before going through the VPN. Next step – your request will be transferred to Tor entry nod which in turn transfers to one or more Tor relays.

The Hidden Wiki & Co
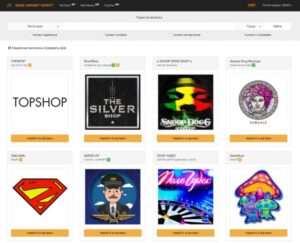
These links typically end in .onion instead of the more familiar .com or .org. Hence Dark Web Links are also known as the .Onion Links sometimes. The service scrambles your Bitcoin with that of other crypto users, affording you complete anonymity. TorLinks is a great alternative to The Hidden Wiki and provides a list of .onion websites across various categories. Sure, there’s some overlap between the two, but the list of sites on TorLinks is widely different. Considering how regularly dark web sites vanish and go offline, it’s better to have more than one source to help you find .onion URLs.
Types Of Dark Web Websites
It was created in 1999 as a secure communication platform for people and groups working on liberatory social change. The platform is protected from government interference and malicious attacks to protect the user. In addition, it ensures that no record of communication is stored. Instead, download Tor, the most secure and user-friendly option for accessing .onion sites. Despite some skepticism about its origins and privacy due to its military development, Tor remains the preferred choice for safe dark web navigation. This part of the internet is notorious for illegal activities, facilitated by the anonymity it offers.
- To access them, copy and paste the hyperlinks provided into the Tor browser.
- This disables potentially dangerous features like JavaScript that could reveal your identity.
- This is especially important for individuals in regions where press freedom is restricted or where government surveillance poses risks to journalists and activists.
- Always exercise extreme caution and verify the legality of any services you access.
Dark Web Sites Offering Financial Services
The website uses an RTA age verifier to prevent underaged users from gaining access, which is yet another plus for safety. The website features any category of content you can imagine, from videos to parodies to original series to porn star content. The most popular content category is definitely full-length movies. Ever since the franchise’s inception, the security has been on point, with no reports of hacking or malware.

Never Share Personal Information
A VPN provides strong security for everyday browsing without the extra delays, middle checkpoint, and then finally the exit gate. The extra connection layers can act as a significant burden to your browsing experience if you’re doing something that is bandwidth intensive. They have an onion site as well, presumably to allow access to the website’s content in countries that aren’t so friendly to the notorious intelligence agency’s … If you make use of a password manager, then it may come with a feature that monitors the dark web for mentions of your email address and password, or any other personal details. It’s something built into the password management services offered by Apple and Google as well, so you don’t need to trawl through data leaks manually yourself. Hackers spend a lot of time on the dark web, and it’s not too difficult to get access to hacking tools and data leaks in this part of the internet.
More From CBS News
It’s still illegal to commit crimes while connected to Tor, regardless of whether or not you think you’ll be caught. Swiss based ProtonMail is an encrypted email service that is quite popular with the cryptocurrency community. It’s a paid service, and while it’s extremely secure you will need another email address to sign up, which can leave traces of your true identity without you realizing. Deutsche Welle (DW) is a German state funded news organization that reports on worldwide topics and events.
You can use this community-edited link database to find everything from anonymous chat rooms, to Dark Web social networks, and blogs about various interesting subjects. In this section, we have listed the most popular resources on the Dark Web. Please note that you must take great care when using the Dark Web as sites often contain adware, spyware, malicious links, and scams. Hacking and cybercrime forums on the dark web are spaces for newbie hackers to ask questions, veteran cybercriminals to share their expertise, and buyers to find sellers. Cybercrime services are more commonly sold through marketplaces, but you can usually find someone offering hacked servers, computer logins, and stolen data on such forums.

Onion sites use The Onion Router (Tor) software to encrypt their connections and enable anonymous communication. Facebook’s onion version lets people access Facebook in countries where access to the social network is otherwise restricted. Facebook’s dark web website helps people around the world connect, communicate, and organize.

It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome. Instead, you need a specific configuration, software, or authorization, such as Tor, to access it. Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal. Facebook’s dark web version allows users to access the site where it is banned or restricted. Although the social application is known for collecting data on its platform, it does not like sharing the information with others. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites.
FAQs About Navigating The Dark Web Safely

Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny. The US Supreme Court has indicated that even casual browsing could lead to legal consequences. The federal investigation which uncovered and shuttered the first dark web site, also led to the closure of three others. “The leadership team that operated one of the sites also operated several of the others.” The takedown of dark web leaders and users also included the convictions of men from Virginia, Maryland, Indiana, Texas, Washington, Arkansas, Michigan and Oklahoma.
Archive.today is considered an important tool to track changes across government and corporate websites, preserve cultural heritage, and keep knowledge outside of autocrats’ reach. You can archive any site you want, or retrieve historical records wherever available. Ahmia promotes transparency by being open-source and allowing contributions. Its operations focus on respecting user privacy and maintaining anonymity through the use of the Tor network. Apparently, Hack-Rent-A-Hacker’s most popular ‘service’ is Facebook account hacking – figures! Anyway, if you’re in this sort of thing, someone can help you get inside a Facebook account for 250 euros.
You’ll keep your identity private while getting results for various Tor websites, forums, and marketplaces. Unlike traditional search engines, it doesn’t track or store personal information, ensuring your searches stay private. It’s a popular choice for users worried about online surveillance and data collection. Typical search engines and standard secure browsers can’t access the dark web. To explore it, you need to install Tor and use a dark web search engine or directory to find and visit onion search engine links.
It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity. The anonymity provided by onion routing comes at the cost of slowing your internet considerably. As such, we do not recommend using Tor if you want to do data-intensive activities like streaming in HD, gaming, torrenting, or making video calls. The biggest and most frustrating part about dark websites is that they live for a short span of time. These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies.
Onion sites are far safer to use as they are hidden deep within the deep web. Also, since users can only access them using the Tor browser (with its high-end encryption), users can be rest assured their identities and locations remain hidden. His articles have appeared in many respected technology publications. Ruheni explains complicated technical concepts clearly and simply. However, most are outdated and have not kept up with the changing landscape.
This is a great way to improve your privacy because Tor isolates each website you visit, meaning third-party trackers and ISPs can’t reveal your identity. The Dark Web is the part of the deep web that is not indexed by search engines, like Google or Bing. For this reason, you cannot browse through these sites using your default search engine. Hence, you never know when a popular .onion site is going to vanish, or even die. Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though). The best thing is to actually understand how to find the fresh, new links.