
Even commerce sites that may have existed for a year or more can suddenly disappear if the owners decide to cash in and flee with the escrow money they’re holding on behalf of customers. All this activity, this vision of a bustling marketplace, might make you think that navigating the dark web is easy. The place is as messy and chaotic as you would expect when everyone is anonymous, and a substantial minority are out to scam others. The Hidden Wiki is a popular onion link directory on the dark web offering categorized lists of sites. Use VPN, avoid logging into personal accounts, enable Tor security settings, and stick to trusted sites. While difficult, tracking is possible if security measures are misconfigured or if users reveal personal information.
The Basics Of Big Data: What It Is And Why It Matters
These sites can be used by both hackers and individuals looking to exploit vulnerabilities. These platforms sell counterfeit or forged documents, including passports, IDs, driver’s licenses, and other official papers. They cater to criminals or individuals seeking to commit identity fraud or avoid legal scrutiny.
VPN Over Tor
Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny. The US Supreme Court has indicated that even casual browsing could lead to legal consequences. The deep web is just the part of the internet you can’t find with a search engine.
Interacting With Online Communities
The Dark Web often carries a stigma, primarily due to its association with illegal activities. However, it also serves as a tool for privacy-conscious individuals, activists, and others who need to operate in secrecy. Aside from government agencies, other entities, including corporations and hackers, could potentially monitor and track your movements across the dark web.
Dark Web Search Engine
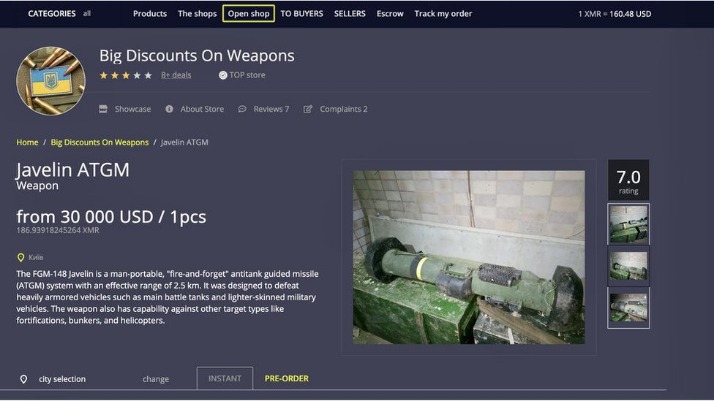
Cybercrime services, such as hacking tools and stolen databases, are available for hire, creating a marketplace for illicit online activities. Dark web monitoring platforms provide secure communication channels for individuals seeking to expose information without fear of retribution. Additionally, the Dark Web serves as a haven for those in censored environments, offering access to restricted information and enabling the free expression of opinions. Illegal Products and Services The Dark Web is rife with websites offering illegal products and services.
It can only be used to access the content uploaded to the Freenet, which is a peer-to-peer distributed data store. Once you upload something, it stays there indefinitely even if you stop using Freenet, so long as it is popular. That information is hidden simply because most users won’t find it relevant. Much of it is tucked away in databases that Google is either uninterested in or barred from crawling. The dark web has no shortage of criminal activity, scams, phishing sites, suspicious links, and malware designed to trick newbies. And because there’s very little use of HTTPS on the dark net, verifying whether or not a website is genuine using an SSL certificate is not feasible.
Navigating The Dark Web Safely
These changes aim to provide clearer guidelines for prosecuting cybercriminals and deterring illegal activities. Legal frameworks focus on the content and transactions conducted on the dark web rather than the act of accessing it. Similarly, in the European Union, privacy laws regulate the handling of personal data and address illegal activities. With its reputation for hosting illegal content, many wonder about the legality of accessing this hidden part of the internet. This topic is significant as it touches on privacy rights, cybersecurity concerns, and legal boundaries in an increasingly digital world.
Using Tor Browser FAQs
There’s no central server to take down, making it incredibly resilient to censorship. However, while Tor hides your location and browsing habits, it does not encrypt the content of your communications beyond the Tor network itself. Visiting a dark web site requires specialized software like the Tor Browser, which routes traffic through a series of random relays across the globe to mask both origin and destination. IOS is the only exception, leaving iPhone and iPad users without the option to go to this part of the internet.
- Download the Linux version from torproject.org, extract the file, and run the start-tor-browser script.
- Websites are usually labeled with registry operators like “.com” and “.org” and can be easily located with popular search engines.
- There are many good and legitimate reasons to step into the dark web, but you should always do so with caution.
- It is important to note that while Dark Web search engines can help users find specific content, they do not guarantee the legitimacy or safety of the websites they index.
- Law enforcement officials are getting better at finding and prosecuting owners of sites that sell illicit goods and services.
Tor Over VPN is when you first connect your computer or mobile device to your VPN service and then use the Tor Browser to travel the internet. While the Tor Browser and the Onion Network are an excellent way to protect your online privacy and anonymity, it is by no means a perfect solution, and it has a few weaknesses. All of this keeps the sender anonymous thanks to how each intermediary node only knows the location of the previous and next node. Each of these nodes removes or “peels” away a single layer, which uncovers the data’s next node destination. When the final layer of the “onion” is reached and decrypted, the message arrives at its destination. All Tor Browser data is encrypted and relayed three times over the Onion Router network, which is composed of thousands of volunteer-run servers, which are known as Tor relays.

It’s designed to offer users complete anonymity and privacy for their online activities, which range across both lawful and unlawful spectrums. Throughout the article, we emphasized the need for security precautions and protecting personal information. We addressed the importance of avoiding illegal activities and scams, recommending that individuals stay informed, exercise caution, and trust their instincts. The Dark Web, a hidden and mysterious corner of the internet, has long held a fascination for many curious individuals. Far from the widely accessible and visible surface web, the Dark Web offers a level of anonymity and privacy that attracts users seeking alternative online experiences.
- Follow this step-by-step guide to safely navigate and explore the Dark Web.
- The threats of online browsing can extend into the unplugged world if your computer or network connection can be exploited.
- Websites on the dark web have .onion addresses, and they operate differently from regular sites.
- In an era defined by digital connectivity, protecting sensitive, critical and personal information from cyber threats – including those originating from the dark web – is a strategic imperative.
- This anonymity is particularly important for individuals living in repressive regimes or those concerned about government surveillance.
Sign up for our newsletter and learn how to protect your computer from threats. To get started, visit the Tor Project website and download the Tor browser. However, keep in mind that Tor itself won’t direct you to dark web sites.
Why Use Tor For Accessing The Dark Web?
However, not all countries are signatories, limiting their effectiveness. TOR is the most popular way to access the Dark Web while shielding a user’s location. Also known as The Onion Router, TOR enables users to browse the Internet, including the Dark Web, anonymously.
Attackers can use tools like keyloggers to gather your data, and they can infiltrate your system on any part of the web. Internet security software like Kaspersky Premium are comprehensive to cover both identity monitoring and antivirus defenses. However, the dark web is also known for being a hub for illicit activity. Anonymous marketplaces (such as The Silk Road) offer everything from recreational drugs and forged documents to firearms and malware toolkits.



