
The replace() function returns a STRING in which all occurrences of a specified STRING in the given STRING have been replaced by another (specified) replacement STRING. The toIntegerOrNull() function converts a BOOLEAN, INTEGER, FLOAT or a STRING value to an INTEGER value.For any other input value, null will be returned. The toFloatOrNull() function converts an INTEGER, FLOAT or a STRING value to a FLOAT.For any other input value, null will be returned. The toBooleanOrNull() function converts a STRING, INTEGER or BOOLEAN value to a BOOLEAN value.For any other input value, null will be returned. The function startNode() function returns the start NODE of a RELATIONSHIP.
That allows me to use the same queries (with references to separate parameters) that I have in my application.You have to wrap the query in your file into a json object for that. Note that each cypher query in the file must end in a semicolon and must be separated by a blank line from the other query. Every PocketSuite account comes with an option to upgrade to a local business phone number for business calls and SMS text. SMS texts have the highest view rate ensuring your clients show up and pay you on time. Under Actions to the right of the Cypher statement is a pencil icon. Click on the pencil to launch the appropriate editing tool for the Cypher statement.
Merge Single Node Derived From An Existing Node Property
Its intuitive design promotes exploration, yet users are advised to navigate with caution and a sense of moral responsibility given the darknet’s nature. Cypher beckons those in pursuit of a novel and evolving adventure into the deeper echelons of the digital realm. The platform is in a phase of development, with its management team focused on rolling out significant improvements to enhance the user experience. Cypher Market has swiftly emerged as a significant entity within the darknet’s commercial landscape, acclaimed for its clean, minimalist aesthetic that places a high emphasis on user experience. Adhering to strict ethical guidelines, especially by excluding certain illicit materials, Cypher establishes a benchmark for conscientious management. Despite hosting a relatively modest vendor base, it boasts an extensive selection of rare and distinctive items, outperforming conventional market assortments.
We’ve built a reputation as the go-to destination for the best cypher link products, and our loyal customer base is a testament to our success. Whether you’re a seasoned cypher darknet enthusiast or a newcomer to the world of cypher link, you can trust that our platform will provide you with the best possible shopping experience. Explore our vast selection, secure in the knowledge that you’re dealing with a trusted and reliable marketplace. Grant ALL DBMS PRIVILEGES privilege to perform management for roles, users, databases, aliases, and privileges to the specified role.
Merge With ON CREATE And ON MATCH
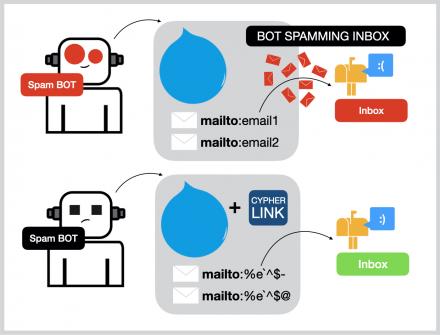
Our mission is to simplify navigation in the complex and evolving world of the darknet. Here, you’ll find links to various resources, including educational archives, private forums, anonymous services, and more. CipherLink is a lightweight, high-performance communication library designed to provide end-to-end encryption for secure data exchange between clients and servers. Leveraging industry-standard AES-GCM encryption, CipherLink ensures the confidentiality and integrity of messages transmitted over the network. See both encoded and decoded versions simultaneously for quick verification and adjustments.
Hydra Darknet Market
Whether you’re a savvy shopper or a discerning connoisseur, our aggregator is your gateway to the ultimate shopping experience. As we look to the future, our cypher link aggregator is poised to redefine the very concept of online shopping. We’re not just a platform – we’re a community of passionate cypher url enthusiasts and cypher darknet market connoisseurs who are committed to pushing the boundaries of what’s possible. Through strategic partnerships, cutting-edge technology, and a deep understanding of customer needs, we’re laying the foundation for a new era of cypher website shopping. Imagine a world where discovery, personalization, and unparalleled convenience are the norm, and where your every cypher url and cypher darknet market desire is effortlessly fulfilled. This is the future we’re building, and we’re excited to have you join us on this transformative journey.
Expansive And Unique Product Assortment
The duration.inMonths() function returns the DURATION value equal to the difference in whole months between the two given instants. The duration.inDays() function returns the DURATION value equal to the difference in whole days or weeks between the two given instants. The duration.between() function returns the DURATION value equal to the difference between the two given instants. The duration() from a string function returns the DURATION value obtained by parsing a STRING representation of a temporal amount. The sum() duration function returns the sum of a set of durations.
Hydra Market Darknet
Use MATCH to find entities that must be present in the pattern.Use OPTIONAL MATCH to find entities that may not be present in the pattern.OPTIONAL MATCH returns null for empty rows. Beginners can conquer Cypher on HackTheBox by grasping the basics, utilizing essential tools, and following a systematic approach. With dedication and practice, conquering Cypher’s challenges is within reach for newcomers in the cybersecurity realm. Cypher Market is a new walletless darknet market on the Tor Network that opened in January 2020. It features escrow and finalize early, and accepts Bitcoin and Monero. This project implements a secure client-server communication system using AES-GCM encryption.
Solana-Based Cypher Protocol Experiences Exploit, Freezes Smart Contract
Create a node property uniqueness constraint on the label Person and properties name and age. An error will be thrown if an attempt is made to create the same constraint twice. If any node with that label is updated or created with a name and age combination that already exists, the write operation will fail. Create a node property uniqueness constraint on the label Person and property name. Using the keyword IF NOT EXISTS makes the command idempotent, and no error will be thrown if an attempt is made to create the same constraint twice.
- From grapes Southern Rhone White Blend, Pinot N Stores and prices for ‘Sine Qua Non Cypher, California’ prices, stores, tasting notes and market data.
- Quantified path pattern matching a sequence of paths whose length is constrained to a specific range (1 to 3 in this case) between two nodes.
- List all database aliases in Neo4j DBMS and information about them, returns only the default outputs (name, composite, database, location, url, and user).
- Function returns the current LOCAL TIME instant using the realtime clock.
- Quantified relationship matching paths where a specified relationship occurs between 1 and 10 times.
The any() function returns true if the predicate holds for at least one element in the given LIST. The rand() function returns a random FLOAT in the range from 0 (inclusive) to 1 (exclusive).The numbers returned follow an approximate uniform distribution. The reduce() function returns the value resulting from the application of an expression on each successive element in a list in conjunction with the result of the computation thus far. The range() function returns a LIST comprising all INTEGER values within a range bounded by a start value and an end value, where the difference step between any two consecutive values is constant; i.e. an arithmetic progression. The keys() function returns a LIST containing the STRING representations for all the property names of a NODE, RELATIONSHIP, or MAP. The duration.inSeconds() function returns the DURATION value equal to the difference in seconds and nanoseconds between the two given instants.

An error will be thrown if the given node is attached to more than one relationship. Create a relationship with the given type, direction, and properties. WITH can be used to remove duplicate values from the result set if appended with the modifier DISTINCT. WITH can be used to assign the values of expressions to variables.
If any other node with that label is updated or created with a name that already exists, the write operation will fail. At the heart of our marketplace lies a carefully curated selection of the finest cypher url products. We’ve scoured the web to bring you the best of the best, ensuring that every item on our platform meets the highest standards of quality and value. Whether you’re in the market for the latest cypher website trends or searching for timeless classics, our marketplace has it all. With our user-friendly interface and intuitive search tools, finding the perfect cypher market item has never been easier.
Banking & Financial Services Specialization
This user will not be required to change this password on the next login. The user will not be required to change this password on the next login. Drop the constraint with the name constraint_name, throws an error if the constraint does not exist. For more information, see Constraints → Create, show, and drop constraints → SHOW CONSTRAINTS. Query the relationship vector index review-embeddings for a neighborhood of 10 similar reviews to the vector given by the query parameter. Drop the index named index_name, throws an error if the index does not exist.



