Once the website is coded, the policies created, the admins ready, and the hosting secured, the site goes live on the TOR network. Buyers won’t come to the site if there’s nothing to buy, and sellers won’t come to the site if there’s no one to buy their products. Server admins will have to either make special agreements to get initial sellers on board, or supply products themselves to get things started. I do not condone the use of DNMs to purchase or sell drugs and other illegal materials online.
Malware Sales
If you want more peace of mind, NordVPN has a dark web monitoring tool you can consider using. This handy feature monitors the dark web for signs that your login details or other personal info have been leaked. Then, you can set up 2FA (two-factor authentication) for that extra touch of security in case someone somehow figures out your password. If you ever have to connect to public Wi-Fi, make sure to use a VPN to keep your browsing safe and private. However, the dark web is so complex and vast that if law enforcement takes down one market, it pops up elsewhere.
Run Antivirus/Anti-Malware Software
In exploring the top 10 dark-web marketplaces in 2025, we’ve examined their core operations, diverse use-cases, inherent risks, and evolving trends. While these marketplaces continue to serve legitimate purposes, such as enabling secure communication and privacy protection, they also remain hotspots for illicit activities and cybercrime. Although dark-web marketplaces utilize technologies like Tor and I2P to enhance anonymity, these methods are not foolproof.
Accessing Darknets
In addition to its emphasis on stolen credentials, 2easy Market offers a variety of cybercrime tools, such as hacking services, exploit kits, and other resources for conducting cyberattacks. The market frequently makes headlines for releasing massive troves of stolen data, often as a way to advertise its services. The market is known for its extensive product listings and reputation system that helps buyers evaluate the reliability of vendors. The Russian Market has been around since 2019 and is one of the more prominent dark web marketplaces. In this post, we’ll walk you through the top 10 dark web marketplaces that you need to watch for potential threats to your organization. Using TAILS is yet another security measure that protects your online identity on the dark web.
VPN Alternatives For Securing Remote Network Access
- To access darknets, users typically need to download and configure the Tor Browser; a modified version of Mozilla Firefox that routes all traffic through the Tor network.
- Vendors with high feedback scores gain visibility, while automated dispute resolution minimizes fraud.
- However, the dark web is so complex and vast that if law enforcement takes down one market, it pops up elsewhere.
- mark it means it has been verified as a scam service and it should be avoided.
- One of the German officers charged with analyzing the contents of the CyberBunker servers told me that the volume of data was unwieldy, but its content fascinating.
|
- But those of us who have studied this space for years weren’t surprised.
- Classic darknet markets sell diverse illegal goods; data stores focus on leaked or stolen data like credentials, databases, and ID records.
- Significant technological innovations and trends have reshaped dark-web marketplaces over recent years.
- Businesses should be aware of the potential for data leaks and invest in data loss prevention measures.
- Its user base is primarily English-speaking, and it appeals to more sophisticated cybercriminals.
}
Those who use these services can still be traced and prosecuted if caught, especially as law enforcement continues to sharpen its tracking tools. Imagine trusting a site where you’ve been buying or selling for months, and everything seems legit. Some marketplace operators first build trust by running a legitimate platform. Unfortunately, the dark web hosts not only explicit but also deeply illegal and disturbing content.
- DarkMarket also advertised itself as being the only such site administered exclusively by women.
- The focus of the investigators was on a 30-year-old German who is suspected of having acted as the administrator of Archetyp Market.
- Purchasing or selling illegal goods—such as controlled substances, counterfeit documents, or stolen data—can result in significant legal penalties, including fines, criminal charges, and imprisonment.
- Even users who access these platforms without intent to buy illegal items risk suspicion or investigation.
- Fill out the form to speak with our team about investigative professional services.
Tor2door Market
The marketplace supports multiple payment methods, including Bitcoin (BTC), Litecoin (LTC), and Cryptocheck. They add new batches of stolen data every other week, and there’s even a bidding system where buyers can place offers on new data batches as soon as they become available. Imagine an underground version of your favorite online marketplace, somewhere hidden, exclusive, and often operating outside legal boundaries. It is similar to an online store, except it’s not the type you’ll find with a quick Google search.
Darknets FAQs
By supplying stolen data, these dark web links fuel many online scams and identity theft operations, playing a critical role in the darker aspects of the internet. Vendors on these platforms undergo reputation-based verification, with detailed feedback systems highlighting reliable sources. The integration of Monero as an alternative cryptocurrency further obscures transaction trails. Markets like Nexus optimize user experience with search filters and discreet packaging guarantees, catering to global demand while maintaining operational security. Thanks to torzon mirror, I’ve discovered a whole new world of torzon market possibilities. The innovative tools, inspiring content, and supportive community have empowered me to explore my creativity and take my torzon darknet skills to new heights.
Search Code, Repositories, Users, Issues, Pull Requests
It has gained a lot of users and has become a popular marketplace due to its focus on security. Buyers can purchase a range of digital goods and services, which include illicit drugs, software and malware, and services related to fraud. The marketplace has over 8,400 listings and 500 vendors who communicate in English and accept Bitcoin for transactions. Despite Telegram’s anonymity, the dark web is still a hot spot for illegal trading of malware, illicit goods, and stolen data (such as stolen credit card information).
STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity. To turn it on, just go to the “Settings” and then the “Tools” section of the NordVPN app and activate “Dark Web Monitoring.” In the end, it’s all about staying one step ahead. The more proactive you are, the better you can protect yourself against identity theft and other cyber threats. They’re tightening security and carefully screening anyone who wants to join. mark it means it has been verified as a scam service and it should be avoided. Payments were not made in euros or dollars, but with the anonymous cryptocurrency Monero, which is particularly difficult to trace. Fill out the form to speak with our team about investigative professional services. Singularity™ Threat Intelligence provides insights into adversary tactics and helps mitigate these risks before they impact your organization.}
Tor2door Market is among the largest dark net shops you must visit in 2025 if you’ve decided to visit such sites. On average, the marketplace consists of more than 11,000 items and 1000 vendors. In April 2016, its APIs were compromised, resulting in stolen messages. But since its relaunch, the developers are focusing more on operational security and ensuring that users can have a good experience on this site.

In this guide, we’ll break down the top dark web markets and how to stay safe while using them. Dark web markets have exploded in scale and reach in 2025, becoming the most dangerous hubs for trading drugs, stolen data, and hacking tools. These anonymous marketplaces—operating mainly on the Tor network—are now a primary threat vector for businesses and cybersecurity professionals.
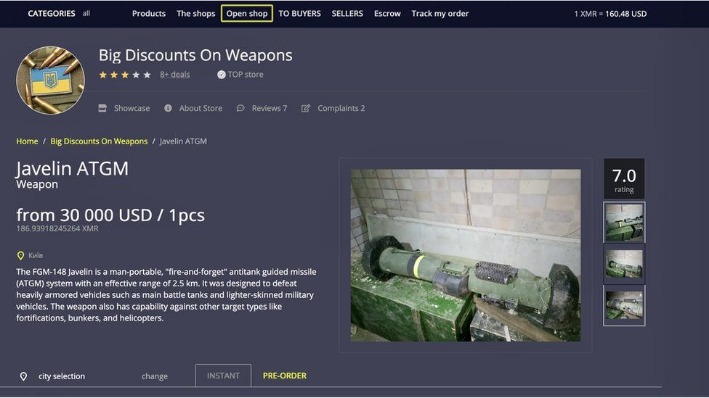
Eventually, the system collapses, and most people lose their entire investment. So, if a “business opportunity” sounds too perfect, it probably is. Surprisingly, most guns on the darknet actually start as legal products. The UNODC (United Nations Office on Drugs and Crime) maintains that almost all firearms are originally manufactured through legal means.
And, of course, think twice before sharing too much personal details online. Even the smallest details about you can be useful to cybercriminals. That all is for general internet activities, you can guess how crucial having a VPN is when you hop onto something like the dark web. Sometimes, you might be hacked by using weak passwords or even just connecting to unsecured Wi-Fi on public networks.
Brandefense’s Dark Web Monitoring is a comprehensive solution designed to continuously track and analyze activity across hidden layers of the internet, including the dark web, deep web, and hacker forums. This solution focuses on identifying stolen data, brand misuse, and potential threats before they can cause significant harm. With Brandefense, businesses gain early visibility into risks that may otherwise remain undetected until it’s too late. Data breaches like the ones mentioned above highlight the significant threats posed by dark web black markets. Stolen data can quickly transition from legitimate systems to underground forums, where it becomes a valuable commodity for cybercriminals. To counter these risks, organizations need robust, proactive solutions that go beyond traditional cybersecurity measures.
It’s a market for fake documents, hacking software, and financial fraud services. WeTheNorth has a strong community vibe, with an active forum where users interact and share updates. It has a search option to let you find local and international products and services on the dark web.



