This website is using a security service to protect itself from online attacks. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data. The Dark Web is a part of the internet that is not indexed by regular search engines and can only be accessed using specialized software. Checking to see whether your data is there takes time, knowledge and effort. A dump of hundreds of thousands of active accounts is aimed at promoting AllWorld.Cards, a recently launched cybercriminal site for selling payment credentials online. Buying and selling stolen credit card information on the dark web is illegal, but it’s a practice now rooted deep in the system.
- From Social Security numbers to bank logins and medical records, cybercriminals buy and sell stolen data every day.
- Monitoring the activity on these platforms is crucial for fraud detection, brand protection, and financial intelligence.
- Even with strict punishments, dark web credit card stealing is at an all-time high.
- The banks, lenders, and credit card companies are not responsible for any content posted on this site and do not endorse or guarantee any reviews.
- Once your personal information hits the dark web, it’s nearly impossible to remove it.
How Do Criminals Get Credit Card Information?
It is illegal and unethical to engage in activities that exploit stolen credit card information. Protecting personal information and ensuring online security should always be a top priority. Buying and selling stolen credit card information is one such illicit activity. This crime is more common than expected, given the strict penalties for this misdemeanor. In fact, according to a 2021 study, approximately 65% of credit card holders have been victims of fraud at some point. The cybersecurity community is on high alert as B1ack’s Stash, a known marketplace on the dark web, has announced a massive leak of 4 million stolen credit card details.

Why Are All The Darknet Markets Down
Instead, one must create strong and unique passwords using a password manager. Especially for your banks or financial accounts, the passwords must be strong and unique to that account only. Hacking in cyber security refers to the misuse of devices like computers, smartphones, tablets, and networks to cause damage to the systems. After hacking a device, cybercriminals can steal any information on users.
How Technology Is Evolving To Counter Card Fraud On The Dark Web
Russian Market is considered to be one of the most popular, reliable, and valuable marketplaces. Unlike the name implies, Russian Market operates in English and doesn’t necessarily have a link to Russia or Russian speakers. These details are needed for physical use such as withdrawing money from ATMs. “We’ve seen these methods employed in the final stages of an attack as a means of covering the criminal’s tracks and maximising profitability,” he said. Law enforcement constantly monitors the dark web, and any involvement in this activity will be considered breaking the law.

For legal reasons, we will not publicly disclose which marketplaces were used. Information in the listings was entered into a spreadsheet for data analysis and statistical calculations. The technique is very profitable in its own right, but it is also used to help launder and cash-out cryptocurrency obtained through other types of cybercrime. Yale Lodge – the largest dark web vendor of stolen credit cards – has suffered a mass exodus of both customers and stolen data suppliers after apparently stealing their funds. Though the vendor is still online and has blamed the issues on “technical difficulties”, it has been banned and removed from all high-profile cybercriminal forums following a major row in June. The detective started chatting with Track2 over ICQ to learn more and he found out that Track2.name was where untrusted customers go to buy stolen cards.
Carding In 2025: How Cyber Criminals Sell Stolen Credit Cards And Teach Fraud
Despite the pseudonymous nature of cryptocurrencies, law enforcement agencies and cybersecurity experts have developed sophisticated techniques to trace these transactions. Now that we understand why individuals are enticed to buy credit cards on the Dark Web, let us explore the risks and challenges involved in these transactions and how to navigate this treacherous landscape. The Dark Web, often mistakenly referred to as the Deep Web, is a clandestine part of the internet that is not indexed by traditional search engines like Google or Bing. It exists on encrypted networks, such as Tor (The Onion Router), which offer users anonymity and protection from surveillance.
Good Password Ideas And Tips For Secure Accounts

In this shadowy realm, hackers can obtain credit card details through various means, including phishing campaigns, malware attacks, and data breaches. Credit cards and the dark web pose a significant threat to individuals and their financial security. The dark web serves as a marketplace where stolen credit card information is bought and sold, fueling illegal activities.
CISOs Brace For Supply Chain Attacks With Proactive Attack Surface Monitoring
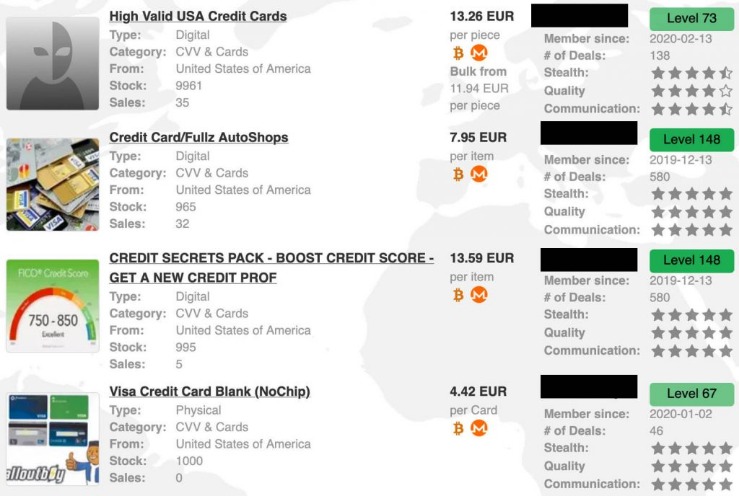
These black markets allow buyers and sellers to make anonymous transactions using a combination of encrypted messages, aliases, and cryptocurrency. Discover the pros and cons of using credit cards or card for purchases, including benefits and risks, to make informed financial decisions. Stolen credit card details can be categorized into different types, making it easier for cybercriminals to exploit them.
- Freshtools is a unique marketplace in that it does not only provide the stolen data, but it allows criminals to purchase MaaS which can cause further damage to the victims.
- To minimize the risk of payment data exposure, only shop from reputable retailers, use digital payment methods or one-time private cards, and protect your accounts with two-factor authentication.
- The intelligence gathered from these markets helps security teams predict and prevent future attacks.
- The pausing/closing feature is especially useful if a specific Privacy Card has been exposed in a data breach or you want to block hidden/unwanted subscription charges.
- “The dumps also include magnetic stripe data, allowing criminals to create physical card clones,” Draghetti warned.
That breach, caused by an attack that compromised POS (point-of-sale) devices, went undetected for nine months. The breach affected 860 convenience stores – 600 of those were also gas stations. PureVPN uses 256-bit AES encryption to ensure safety even when connected to a public WiFi network.
Becoming familiar with their techniques can help you retain control over your money. Your personal information can sell for upwards of hundreds or even thousands of dollars on the dark web—and you might not even know it’s even out there to begin with. Using a random WiFi network is unsafe as it is like a hot spot for all scammers to plant malicious software into your devices.
Carding is packaged and sold like a legitimate business within criminal communities—often mimicking the tone, structure, and customer service you see in e-commerce. This gives security teams time to adjust their defenses before new techniques become widespread. Early detection enables your security team to prevent a transaction, minimizing the risk of a chargeback. I can’t stress this enough, your point-of-sale systems should never share a network with general-purpose computers or IoT devices. For example, requiring additional verification for purchases that deviate from a customer’s normal pattern, rather than forcing verification for every single transaction. Instead of storing actual card numbers, each card should be converted into a unique token.
By adding an extra layer of authentication, financial institutions reduce the risk of fraudulent activities during transactions. This proven technology, seamlessly working in the background, analyses transaction data and authenticates users in real-time, ensuring only legitimate transactions proceed. Additionally, securing transactions with a 3-D Secure ACS (Access Control Server) solution plays a pivotal role in bolstering the overall fraud prevention strategy. With stolen payment cards, a cybercriminal can immediately make purchases under your name, or even drain your bank account.
How Can I Protect My Credit Card Info?
Carders tend to target specific sites that don’t have VBV or other protections against fraud. For fledgling criminals who don’t know how to use stolen credit cards, there are plenty of free and paid tutorials for carding on the dark web. Using PureVPN’s Dark Web Monitoring is an effective way to check if your credit card details are circulating on the dark web. It continuously scans dark web marketplaces and forums for exposed personal data, including credit card information. To protect yourself, it’s crucial to monitor your credit regularly, report any suspicious transactions promptly, and use secure payment methods online.
Collecting used keystrokes is how hackers typically guess credit card numbers, PINs, and passwords. Using a public Wi-Fi network for payments is a major security risk as hackers can easily intercept the transmitted data. Unsecured Wi-Fi networks are prone to man-in-the-middle attacks, where a hacker intercepts the exchange between two parties—often by compromising the router—and gains access to sensitive data. Experian’s free credit monitoring service is one easy way to stay alert. It tracks changes to your credit report and helps you spot potential identity theft early, so you’re not the last to know when something goes wrong.
Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down. These stolen cards have value because they can be used to purchase high-value items or gift cards, which can then be resold for cash. This latest pack is the fourth credit card dump the carding market has released for free since October 2022, with the previous leaks counting 1.22 million, 2 million, and 230,000 cards.



