
Many email services, citing security reasons, require a phone number for identity verification. This creates an unfortunate paradox in which you must give up a highly sensitive piece of personal data to Big Tech. We offer this feature primarily as a convenient way to access onion sites using your regular browser, and it does offer some security advantages over using Tor Browser. Still, if security is important to you, we strongly recommend reading through the Tor Project’s official advice on using Tor and VPNs together(new window). With darknet, you only connect to trusted friends who you’ve previously exchanged public keys and node references with.
The Deep Web refers to all web pages that search engines cannot find. Almost all sites on the so-called Dark Web hide their identity using the Tor encryption tool. You may know Tor for its ability to hide your identity and activity. You can use Tor to spoof your location so it appears you’re in a different country to where you’re really located, just like when you use a VPN service. The dark web came into existence as an offshoot of government experiments with anonymous communication.
VPN Over Tor (Not The Best Option)
Take a look at the sites that these directories have collected and see what topics interest you. People mostly use it for covert communication, anonymous tips submission, and stuff like that. Services like Random Chat connects you with random people using the same service.
Impact Of Law Enforcement And Policy Changes

Norton 360 Deluxe provides a comprehensive suite of protection that can help block malware and dangerous links in real time, and even detect scams using cutting-edge AI detection. Plus, it features a built-in VPN to encrypt your connection, hiding your IP address and online activity, for more anonymous and private browsing. Knowing if your information is on the dark web is a critical part of protecting yourself from threats. Dark web monitoring tools are similar to a search engine (like Google) for the dark web. Users of the dark web should also realize that although their activity is technically anonymous, associating with people who are conducting illegal activities can have legal implications.
As we delve deeper, we’ll explore the dark web’s true nature, its uses, and why it merits our attention. However, the dark web has gained a negative reputation as a forum for those who want to use it for illicit activities. However, some may abuse the power of the dark web by making it easier to engage in criminal activity. While the dark web promises privacy to its users, it can also be used to violate the privacy of others. Private photos, medical records, and financial information have all been stolen and shared on the dark web. Tor Browser prevents someone watching your connection from knowing what websites you visit.
Don’t Provide Personal Information
After that, browse .onion websites through dark web directories or search engines, being careful to follow proper security practices. The history of the Dark Web as a hidden network is tightly connected with the history of anonymous technologies and encryption. From the time of its emergence (the mid-1990s), government agencies have experimented with onion routing to protect communications of sensitive information.
Tips To Stay Safe When Using The Dark Web

On the other hand, the dark web hosts marketplaces and forums where illegal goods and services—such as drugs, weapons, and stolen data—are traded, making it a hotspot for criminal activity. Despite its negative reputation, not all activity on the dark web is malicious; some users rely on it as a tool for freedom of expression or to circumvent restrictions. Dark web sites are hidden by non-indexing, making them completely anonymous. You’ll need a purpose-built browser that uses The Onion Router (TOR) to access dark web content.
But navigating the dark web is full of cybersecurity and legal challenges. A large portion of activities on the dark web involve illegal content, transactions, or services. Simply accessing certain sites or engaging with the wrong links could implicate you in criminal investigations. Though it is not illegal to visit the dark web, accessing it can expose you to serious legal risks, even if you don’t have any criminal activity in mind. Though there are other ways to access onion websites, it is recommended that you always use Tor to access dark web websites.
In particular, you will need a VPN connection and a secure web browser (such as the Tor browser). Depending on your needs, you may want to use your VPN to download the secure browser of your choice. The average person doesn’t share their private life with just anyone; they let specific people know about it when the information is needed. For example, you might tell your closest friend about a problem in your personal life, but you would not tell the clerk at your grocery store. The “deep web” includes everything on the internet that is password-protected, paywalled, or even just protected from crawling by a site’s robots.txt file.
Government Monitoring
Go to the Proton Account signup page in a web browser on your computer, and pick the Proton Free account option. Many organizations, including Human Rights Watch(new window) and the Electronic Frontier Foundation(new window), also support the use of and access to the dark web. For similar reasons, the dark web is more resistant to surveillance. Whistleblowers, journalists, and other professionals at risk of targeted surveillance use the dark web to communicate sensitive information. For example, whistleblower Edward Snowden used TAILS(new window) to help stay one step ahead of the NSA. Because of their closed nature, these darknets also make it impossible to know how many people actually use Freenet.
What Are Autoshop Marketplaces

Microsoft Word is one of the best word processors around, allowing you to craft powerful documents with an intuitive interface. If you know how to use Microsoft Word, you’re typically working with large files that span multiple pages. So, you’ll be happy to know there are several easy ways to delete a page in Word, including both blank pages and those you simply no longer need. We already went through VPNs, anonymizing web browsers, and disposable operating systems, so I won’t bother reminding you about those.
Surface Web Vs Deep Web Vs Dark Web Vs Darknet
- Here’s everything you need to know about this other internet, as well as how to access it.
- It is a reliable messaging tool where you copy/paste a text or image and send it to your addressee.
- Regardless of its nomenclature, this is by far the safest option you can go for.
- Beyond this “surface web” is the deep web, and within the deep web is the dark web.
- However, there are plenty of legitimate reasons to use the dark web.
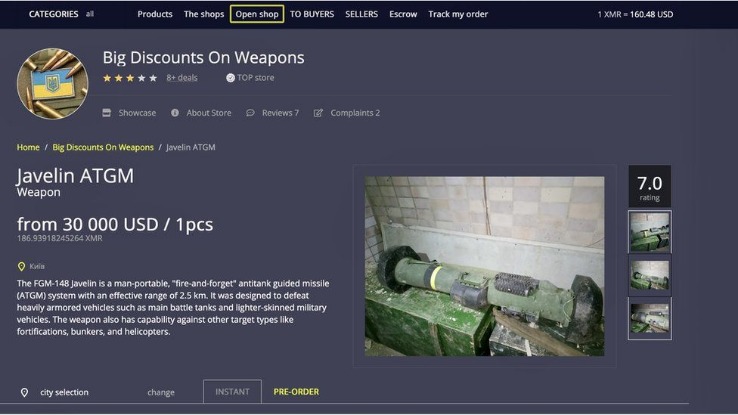
These sites are often closely monitored by law enforcement agencies and are illegal to access or participate in. Dark web encryption allows website owners and users to stay completely anonymous during their engagement. The high level of anonymity is the main reason the dark web is replete with illegal activity, from drug dealing and arms trafficking to the sharing of exploitative content and stolen login credentials. Regular dark web visitors know that it’s possible to exploit the sketchy reputation of the space and the services offered. And though some dark web marketplaces offer user reviews, not all do.
This is especially true, they say, to help law enforcement track criminal organizations and illicit activities. Ruheni Mathenge specializes in writing long-form content dedicated to helping individuals and businesses navigate and understand the constantly evolving online security and web freedom worlds. His articles have appeared in many respected technology publications.

If you decide to venture into the dark depths of the deep web, make sure you’ve bolstered your device’s security with powerful privacy and security tools that can defend against dark web threats. Install Norton 360 Deluxe to help secure your device, block scams, and stay private online. Download Norton 360 Deluxe to help secure your device, block scams, and stay private online. Despite its legitimate uses, cryptocurrency’s untraceable payment nature has raised concerns around money laundering and illicit trade, driving regulatory scrutiny. This guide will teach you how to install the Tor Browser in Windows easily so you can access the Dark Web or browse the web anonymously.
Instead of search engines, you’ll need to rely on directories or specific .onion links. For an additional layer of security, consider using a Virtual Private Network (VPN). A VPN enhances your anonymity by creating a private network from a public internet connection. It allows you to mask your location and obscures your online activities, making it more difficult for cybercriminals to track you.



