“We are seeing children at a very young age having access to devices. Some of this material is self-generated but what happens when the device needs to go for repairs? That material gets backed up and you never know where it’s going to end up”. While it is recognized that the darknet was initially used to create an application or modus for free speech, particularly in areas of political conflict, in reality, its anonymity has rendered much of the darknet a criminal marketplace. As per the Global Commission on Internet Governance (Global Commission on Internet Governance 2015), “the darknet certainly is the seedy underbelly of the Internet.
Examining CSAM User Behaviour
So, search results won’t be based on your browsing history, location, or anything else. And I liked that if I visited a site that had a .onion version, it prompted me to switch to that version. There’s also a much more sensitive proposal that could only proceed with government approval. Companies could train AI models on fake child sexual exploitation images to build more sophisticated detection systems. Without proper safeguards, though, that route could result in companies developing AI models that are even better at producing even more lifelike images.
If you are engaging in the use of the dark web and have been charged with Internet sex crimes, it’s critical to work with an experienced sex crimes attorney who can help you protect your rights. As well as studying the security precautions taken by online CSEA offenders, researchers have considered the types and nature of interactions between members of these online communities in the Surface Web. Holt et al. (2010) note that such communities are self-policing in that members police one another’s behavior to avoid security breaches. Security measures and avoiding detection are therefore a common discussion topic in such communities on the Surface Web (see also Quayle and Taylor, 2001; Davidson and Martellozzo, 2008; Europol, 2015). Members also offer advice, and share ‘tips’ with one another, on accessing victims (Quayle and Taylor, 2001; Davidson and Martellozzo, 2008; Europol, 2014, 2015; Web-Iq, 2018). A VPN protects your connection against everyone, not just your ISP and the authorities.

Materials And Methods
Keybase also offers extremely user-friendly secure chat and file-sharing services through its app. Keybase is an exciting identity service that aims to make it easy for you to link the presence of your online identities together in a cryptographic way. You can upload your PGP key or have the site create one for you, and use it to cryptographically link your Twitter profile, Github account, or Bitcoin address together. Based in Switzerland, ProtonMail is an encrypted email service that is very popular with cryptocurrency enthusiasts. The process costs a fee, but unlike other “tumbler” or “mixing” services, there is no risk that Wasabi or any of its users could scam you out of your coins. Archive.today is considered an important tool to track changes across government and corporate websites, preserve cultural heritage, and keep knowledge outside of autocrats’ reach.
It’s going to be sealed in a moisture barrier bag so the dogs can’t smell it. You are more likely to be caught if it’s coming from a highly-flagged country like the Netherlands. For a couple of years I drank the Kool Aid, I really believed in his vision and what he was doing with Silk Road.
Warm Hubs Also Offer Social Life -council
Make Tech Easier provides tech tutorials, reviews, tips and tricks to help you navigate the complicated world of technology. Connecting to a .onion site via the Tor browser involves routing your connection through several nodes, each adding a layer of encryption. However, this layered approach can expose you to potential risks, which is why using a VPN is strongly recommended. Proving the dark web’s expanding role in criminal transactions is difficult. Knowledge, funding, and resources for probing the marketplace are insufficient to overcome the legal and technical challenges facing investigators. ● Line officers must learn the scope and common types of illegal dark web dealings.
- A VPN protects your connection against everyone, not just your ISP and the authorities.
- To serve these people, several independent news outlets offer onion mirrors, making them invaluable sources of information.
- The WeProtect Alliance’s 2019 Global Threat Assessment report estimated there were more than 2.88 million users on ten forums dedicated to pedophilia and paraphilia interests operating via onion services.
- The year was barely half over, and Chief Farnsworth’s team had already conducted about 150 such raids across Utah.
- However, there are some significant variances in the background despite the similarities.
Is It Legal To Access Dark Websites?
The only way to access Tor sites that the Tor Project recommends is to use Tor Browser(new window), a modified version of Firefox that routes all connections through the Tor network by default. Tor was originally an acronym for The Onion Router, which references Tor’s multiple layers of security. While it can’t know your real IP address, it can see your unencrypted data, which may reveal your true identity (although HTTPS(new window) still protects you). The dark web has an entirely justifiable reputation for being a place where bad things happen. However, the fact that it’s almost impossible to censor the dark web also makes it invaluable for accessing legitimate content that might otherwise be censored. A recent effort led by German police, and involving others including Australian Federal Police, Europol and the FBI, resulted in the shutdown of the illegal website Boystown in May.

Dark Web Links For Information Resources
- With the sheer quantity of child sexual abuse material showing no sign of slowing, the IWF is now working to improve its automated systems to do more without human analysts needing to intervene.
- Not every visitor is a criminal, but this is where most cybercrimes begin.
- Many news publications, like the ones listed above, have a SecureDrop on their .onion sites.
- This would verify if it’s a browser issue or just an issue with the site.
- Although this is one possible assessment method and yields the ground truth, we do not download, open, or view any media content in this research, rather solely focus on textual data.
- Typically, when people talk about the “dark web”, they almost always mean Tor websites.
It also keeps the graphical copy and text of the page for better accuracy. The social media giant is also aware of the many attempts by repressive regimes to restrict its access. After all, it enables users to connect and communicate with each other from around the world. It allows you to search for images, maps, files, videos, social media posts, and more. It will offer you an additional layer of encryption to access the deep parts of the internet. If you know the right websites, you can easily access a tremendous amount of information, including research articles, news stories, and more.
Relation To Other Sex Crimes

In 2023 alone, there has been a significant rise in “nudification” bots globally, with Telegram playing a major role in this rapid growth. In AI-Generated ‘Undressing’ Images Move from Niche Pornography Discussion Forums to a Scaled and Monetized Online Business, researchers note that Telegram is often the source of the creation and dissemination of SSEM technology. Every app this dangerous man used to prey on children could have prevented the exploitation from happening. In a February 2024 study, Tech Platforms Used by Online Child Sexual Abuse Offenders, Telegram was noted as the #1 most popular messaging app used to “search for, view, and share CSAM” by almost half of the offender respondents (46% Telegram, 37% WhatsApp).
Is It Safe To Visit onion Sites On The Dark Web?
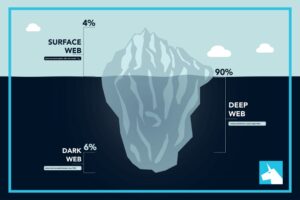
The dark web is a part of the deep web that contains websites not included in the mainstream search engine index. The deep web is not a series of sites but a storehouse of records, including email accounts, medical records, private messages, and more. Since privacy and security are a concern while using the dark web, the websites you visit must have the encryption necessary (HTTPS, preferably) to protect you. Riseup is a dark web platform that offers secure messaging solutions. It does not store logs and is protected from interference and malicious attacks.
Intervention For CSAM Users

Based in Germany, the exchange platform provided pedophiles worldwide with photos and videos of severe child abuse. Many dark web links could get you mixed up in some kind of criminal activity of another, whether you’re looking for it or not. The deep web is rife with sales of illicit drugs, weapons, and goodness knows what else, and steering clear of these nefarious web pages is easier said than done. Viruses, ransomware, and other types of malware are more common on onion sites than on the normal internet. Many pages have poor encryption standards and no other protections, so simply visiting a Tor site can infect your device. Since most Tor websites are non-indexed and unregulated, the probability of scams is much greater on the dark web.

Blockchain.info (now Blockchain.com) is a popular cryptocurrency wallet and blockchain explorer service (one of the first sites to launch on the dark web). It was initially created to provide additional security and eliminate cryptocurrency theft. It’s a wallet, explorer service, not a dark web marketplace itself, but still a helpful resource. You are not required to provide your personal information to create an account. The email service is available both on the surface and on the dark web.