The common search engines for the Dark Web like Grams, are not very useful. However, these .onion websites are never displayed in Google search results. It gives you an additional layer of encryption and anonymity—backed by a strict no-log policy. Try it yourself and get a full refund within 30 days if you’re not satisfied.

Robotsnet Uses Cookies To Improve Your Experience And To Show You Personalized Ads Privacy Policy
Your ISP only sees the encrypted VPN traffic and won’t know you’re on Tor. A logless VPN, which doesn’t store any traffic logs nor session logs is highly preferable. Traffic logs are a bigger concern than session logs, but neither are good. To begin with, it’s important to understand that the Dark Web is not inherently illegal or dangerous, despite its reputation. However, it is also a place where illegal activities can and do occur, so caution is advised. The dark web is a part of the internet that is not indexed by traditional search engines like Google or Bing.
How To Protect Yourself While Browsing The Dark Web Safely In 2025/2024: Step By Step
A VPN adds that extra layer of privacy you need when browsing the dark web on Tor. Tor hides your IP address by routing your traffic through multiple encrypted layers, but that’s only in the Tor network. Your ISP (Internet Service Provider) or anyone monitoring your connection, like a network administrator, can still see you’re accessing the dark web.
From this point onwards, you can enjoy complete anonymity and security while being able to access “.onion” websites and other dark web browser domains. Now that you’ve completed the download, it’s time to install the Tor browser on your device. (The installation instructions that follow are for the macOS platform, I’ll mention where it’s different for Windows.) Simply double-click the downloaded file in your download folder. When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI.
How Do I Safely Access NotEvil Dark Web Search Engine Without Risks?
Stay informed about the latest security practices and developments related to the Dark Web. Regularly educate yourself about new threats, scams, or vulnerabilities that may arise. This will help you adapt your browsing habits and maintain a safer online experience. Avoid downloading files from unknown sources while browsing the Dark Web. Malware, viruses, or other harmful software can be disguised as innocuous files. Once the Tor Browser is launched, it may take a few moments to connect to the Tor network.

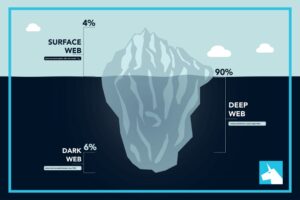
Privacy and anonymity are the dark web’s hallmarks, thanks to a network of servers that hide users’ identities and locations. The Dark Web is a hidden part of the internet, completely different from the clear web we all use daily. When you search for something on Google or Bing, you’re using the clear web. What if your biggest cybersecurity risk isn’t a hacker in a distant country, but someone with a co… Struggling to find a simple way to access shared files across your company network? Regular browsers access much of the deep web, especially sites behind logins.
- The Tor Browser will automatically connect to the Tor network, establishing a secure and encrypted connection.
- Fake sites are everywhere, and even a one-character difference in the URL can land you on a phishing page.
- That’s why such a large percentage (as much as 94%) of the entire web is not returned in Google Search.
- The Dark Web is a fascinating and mysterious realm of the internet that offers both benefits and risks for those who choose to explore it.
Step 6: Access The Tor Browser On Tails OS
Tor is a special browser and the most popular choice because of its security features. These anonymous browsers provide safe and secure access to users on the dark web. A browser like Tor offers various features, including data security through layers of encryption, hiding your IP address, preventing online tracking, and much more. Now that you understand the essentials of anonymous networks and how to prepare yourself for secure browsing, it’s time to explore the practical steps involved in accessing the Dark Web. While the process is not overly complicated, it demands attention to detail, adherence to best practices, and an understanding of the risks. Put simply, the deep web is all the information stored online that isn’t indexed by search engines.
Step 2: Install Privacy-Focused Browsers
Frequently mimicked by clones and scams, the “authentic” Hidden Wiki requires verification via trusted Tor forums (e.g., r/onions on Reddit). Its simplicity and structure make it ideal for beginners, but its lack of keyword search limits depth for advanced users. Its minimalist interface—unchanged in over a decade—prioritizes raw functionality, delivering a firehose of results for users willing to sift through clutter. Torch supports both V2 and V3 .onion addresses, ensuring compatibility with older and newer sites. Ahmia’s filtering kept me away from shady marketplaces peddling stolen data, saving me from potential scams. However, when I searched for a specific blockchain-related forum, Ahmia returned only two results, and I had to use Torch for broader coverage.
#1 Install A VPN
In some parts of the world, simply using a browser like Tor can get you flagged by these agencies, even if you don’t partake in illegal activity. Most URLs on the dark web have unrecognizable names, so it’s easy to fall for this trap — putting your private files, financial data, keystrokes, and other personal information at risk. Social engineering tactics are also common, where bad actors try to get you to willingly give up sensitive information, like login details, financial information, etc.
Additionally, ensure that the VPN service has a wide network of servers in various locations to offer you more options for server locations. Before accessing the Dark Web, carefully weigh the potential benefits against the risks involved. Ensure that you are aware of the legal implications, take necessary security precautions, and approach any transactions or interactions with caution.
Allowing Port 80 Connections (Firewall Configuration)
Use the tips below to patch common blind spots and avoid easy-to-make mistakes. Don’t log into any real accounts, reuse usernames, or enter any personal details. Treat every site as untrusted unless you’ve verified it from multiple sources. The deep web refers to portions of the internet not indexed by standard search engines. This includes everything from academic databases to medical records, government resources, and confidential corporate documents stored behind login credentials.
It is also important to use common sense and trust your instincts while navigating the dark web. If something seems too good to be true or too risky, it is best to avoid it altogether. Additionally, using reputable directories and link lists can help you find what you’re looking for on the dark web without exposing yourself to unnecessary risks. Navigating through corporate investigations is a complex but essential task to ensure your company’s resilience against internal threats. Covering everything from uncovering fraud to protecting proprietary information, these investigations not only address urgent concerns but also prevent future risks.