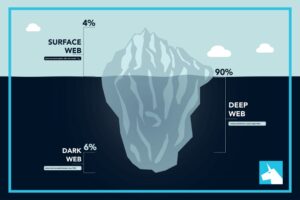
It’s the underground Internet that you can only access through special software, and it’s full of dangerous activity. The dark web hides your location and identity, so it is frequented by teens who want their digital activities to stay hidden. Our app, Safes, is designed with a deep understanding of modern parenting challenges. It offers features such as real-time location tracking, screen time management, and content filtering, empowering you to guide your child’s digital interactions effectively.
- The majority of the web is called the “deep web” (often referred to as the “invisible” or “hidden” web).
- We propose an intervention strategy based on our observation that some CSAM users do indeed recognise their problem.
- Millions of customers’ personal data, including names, addresses, bank account and credit card account information, and many other forms of sensitive data.
- It offers a Reddit-like interface, where you can learn everything you need to know about darknet websites and spotting the real from the scammers.
- The world’s “largest” dark web child porn site, which boasted “more than a million” downloads, was shuttered after international authorities said they followed a seedy trail of Bitcoin transactions.
Trusted Directories And Forums (stay Away From Hidden Wiki)
Check around with other users and ask if they know anything about the new marketplace. Unfortunately, it’s also a place where the bad guys can offer their services – for example, hackers or hitmen. Opennet connections are easier to use, but darknet connections provide more security against attackers on the network. In opennet mode, the network will automatically assign you to other users on Freenet’s network. As I mentioned previously, the dark web is quite popular with journalists, political bloggers and news publishers, and others who run the risk of imprisonment in countries like Iran and others.
What Is The Darknet?
Although a relationship may be initiated in a chat room or social networking site, they can continue through text, email, or through the use of other apps. In 2014, Australian police took over and eventually shut down a site called The Love Zone, arresting its administrator and a number of users too. The following year, the FBI closed Playpen, which was, at the time, the largest dark web child abuse site in existence.
The Dark Side Of Online Gaming

It is also important to recognize the risk of youth crossing boundaries with other youth online. Youth can also face legal consequences for child sexual abuse material despite their own status as a minor. It may seem like the best solution is to restrict or remove access to digital media, but this can actually increase the risk of harm. A youth may then become more secretive about their digital media use, and they therefore may not reach out when something concerning or harmful happens. Instead, it’s crucial that children and youth have the tools and the education to navigate social media, the internet, and other digital media safely.
Measuring CSAM Searches On The Tor Search Engine
Detailed insight into the patterns of online behavior that characterize these subgroups may be used to provide insights for intervention efforts. Distinguishing subgroups of CSAM groups may also aid preventive efforts, as some forum members may be more receptive to interventions than others. Presenting individuals searching for CSAM on the darknet with warning banners emphasizing the illegal nature of their actions may help to prevent some of them from entering CSAM forums altogether (Prichard et al. 2022). Upon entering the forum, the user usually sees separate sections for pictures, videos, and further content. In addition to CSAM pictures and videos, the communities maintain large textual sections. The discussion areas are often provided in many languages including ones that are not widely spoken, such as Czech, Hungarian, or Scandinavian languages, reflecting the global reach of these CSAM communities.
“He was asking her to shake her bum, take off her top and trousers, which she thankfully did not do.” “These people were saying she was beautiful, hot, sexy. She told them she was only eight years old and they were OK with that. She witnessed a man masturbating and another man wanted to play truth or dare with her. According to new research collected by data analyst Semrush, Omegle grew globally from about 34 million visits a month in January 2020 to 65 million in January 2021. Despite the lack of physical contact, it is still considered abusive behavior for an adult to be engaging with a minor in this way. Adults may offer a young person affection and attention through their ‘friendship,’ but also buy them gifts both virtually and in real life. They look to try and isolate a child from their support network and create a dependency so that they establish a sense of power and control over the child.
Worried About Your Child And Online Porn?

The seizure last year of Son’s web server uncovered approximately 8 terabytes of videos depicting child sexual exploitation — considered one of the largest seizures of its kind, according to the Justice Department. He went on to present a map of the United States covered with red dots, each representing a computer used to share images of child sex abuse. Fewer than two percent of the crimes would be investigated, he predicted. “We are overwhelmed, we are underfunded and we are drowning in the tidal wave of tragedy,” he said.
The Hidden Wiki
During these five years, search engine users performed 238,794,231 queries. We analyse these search phrases to determine what Tor users are seeking primarily from onion services. Web crawling as a method is biased towards websites that are frequently linked, and it cannot locate onion websites if there are no links to them.

For example, vendors selling stolen data or illegal substances often conduct transactions exclusively within Telegram’s ‘Secret Chats,’ utilizing self-destructing messages and end-to-end encryption. They further obscure their identities by employing virtual phone numbers and conducting financial transactions using cryptocurrencies, minimizing the risk of attribution by law enforcement or rival cybercriminal groups. This focus on personal OpSec underscores the challenges faced by cybersecurity professionals attempting to monitor and disrupt these activities. Tor, or The Onion Router, is an anonymising system that lets people use the web without revealing who they are or which country they are in. The anonymity offered by the network has encouraged many people to set up hidden .onion sites that offer content, services and goods that it is illegal to sell openly. Why does the Tor network allow such abhorrent material to remain, despite extensive opposition — sometimes even from those within these groups?
The survey does not request any personally identifiable information from respondents – such as age, country, or gender – that would put privacy at risk. Questions avoid specifics of criminal conduct (e.g., time, date, place, or victim details). We ask CSAM users about their thoughts, feelings, and actions related to their use of CSAM so that in the future we can build a cognitive behavioural theory-based anonymous rehabilitation programme for CSAM users. We demonstrate that not only are CSAM websites widely hosted through the Tor network, but that they are also actively sought.
The rise of online gaming has attracted unwanted attention from criminals looking to groom children. The Dark Web can be accessed through particular software and programmes. The software anonymises the user through directing all requests to a centralised source, and randomly redirecting it. It is known as “The Onion Router” as it promises layers of encryption, meaning a user could not be traced.
Report It To The Authorities (if It’s Safe To Do So)
They know how to process the information and get it to the correct law enforcement agencies internationally. All in all, it is not illegal to access the dark web, but it can create issues for you. If you don’t take the necessary measures, many unsavory activities can expose you to unnecessary risks. Initially, the dark web was mainly used by government agencies, big businesses, hackers, and cybercriminals.