Some sites might use these details for advertising, analytics, or tracking your online preferences. In most cases, choosing “Connect” will allow you to connect to the Tor network without any further configuration. In the “Language” settings, select your desired display language from the dropdown menu. It offers outstanding privacy features and is currently available at a discounted rate. Second, shutting down or controlling access to the dark web would be a huge undertaking and could have unintended consequences. Finally, many people consider the dark web a necessary tool for privacy and freedom of speech.

What Is The Onion Network?
While Tor lets you reach .onion sites, many require invitations, passwords, or verification. The dark web marketplaces thrive on the demand for illegal services and extreme content. Your accidental visit to such sites can contribute to the perception of the demand, encouraging criminals to continue or expand their operations.
Commercial Services

Riseup is a volunteer-run collective that offers secure chat and email services primarily used by progressive activists and social justice communities. It’s maintained by an independent organization committed to digital privacy and security. It runs an onion site to help like-minded people mobilize more securely and anonymously. Proton Mail is an anonymous email service that operates an onion site. It is a useful tool for people who value their privacy and want to protect their communications with default end-to-end encryption, zero-access architecture, and minimal personal information requirements. Below, we list some onion sites you can explore relatively safely.
While the Tor network was not created for illegal activities, as it’s harder to trace websites to their physical location, cybercriminals have also adopted it to host their websites. While Tor offers strong privacy protections, it comes with notable drawbacks that can make it impractical for everyday use, and the dark web content it grants access to can put users at risk. Unlike Tor, I2P is designed for peer-to-peer services like file sharing, email, forums, and even decentralized websites — all within its own closed network. Its distributed nature makes it more resistant to central points of failure. Tor is the most popular way to access the dark web, but it’s not the only option.
Step 7: Use Additional Security Tools

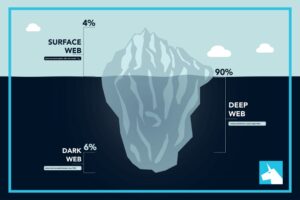
Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity. The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing. It means you cannot access websites on the dark web with regular browsers like Firefox or Chrome.
- The Tor Browser stands as a specialized tool in the realm of internet navigation, designed to grant users enhanced privacy and anonymity while online.
- It is a realm that demands both mindfulness and education about the risks and ethical considerations involved.
- Just note that although you’ll be anonymous, you won’t have the speed or convenience of a direct connection, and some sites might block you outright.
- Research what they offer and assess your privacy needs to make a decision about which dark web browser works best for you.
- Additionally, contact the Social Security Administration to report the breach and discuss further protective measures.
Be Cautious With Downloads

This added layer of security keeps your identity hidden and shields you from online threats. Since regular search engines don’t index .onion sites, finding what you need on the dark web can be tricky. That’s where dark web search engines come in — they help you discover hidden websites and make navigating this part of the internet easier.
- You can download Firefox on desktops (Windows, macOS, Linux) and mobile devices (iOS and Android).
- Whether you’re a journalist, an activist, or simply someone who values privacy, Tor can give you an unprecedented level of online anonymity.
- The exit node knows what you’ve requested and connects you to it, but it doesn’t know your device and its IP address.
- However, remaining anonymous can be invaluable to protesters, civil rights groups, journalists, lawyers, and other vulnerable groups.
- DigDeeper offers in-depth analysis of technology and privacy topics rarely covered by mainstream media.
Browse Privately
While this is not much compared to standard email services, it is enough for PGP-encrypted messages. The Tor Metrics is a good place to get more information about the Tor project. It collects data from the public Tor network and archives historical data of the Tor ecosystem.
It will offer you an additional layer of encryption to access the deep parts of the internet. This article lists some of the best dark web websites you can visit securely. Some of these sites are very helpful (but unseen as Google doesn’t show them), while others are just for fun.
Only Use HTTPS Sites

The Tor browser is able to access the special domain names, with the suffix .onion, used in the dark web. Yes, you can still be tracked on the dark web despite its privacy features. Tracking can happen through IP leaks, browser vulnerabilities, or malicious exit nodes. To reduce this risk, use the Tor Browser properly, keep your software updated, avoid sharing personal information, and pair it with a reliable VPN.
Freebie VPNs will track their users’ online usage, as they make money by selling this tracking info to advertisers and other nosy parties. Other options are the Freenet and I2P (Invisible Internet Project) peer-to-peer networks, both of which provide censorship-free communications. While the iOS solution is not an official one, the Tor Project links to it, providing the browser its tacit approval.
While anyone can use it, it’s built for high-stakes exchanges, making it overkill for routine file sharing or data backups. Major news outlets like The New York Times, The Economist, and The Guardian host SecureDrop instances on the dark web to give sources a safe, anonymous way to share sensitive information. But while anonymous email services can help protect your identity, they don’t make you immune to threats like email spoofing or social engineering.
How To Get Started With Tor Browser – A Web Browser Designed For Privacy
This means you can use your favorite browser instead of the Tor Browser and still benefit from being routed through the Onion Network. While there are numerous VPN services that work well with Tor, I’ve found that NordVPN offers the best protection and compatibility, and keeps your personal information safe. A secure VPN server slows down your browsing much less than the Tor Browser and also opens access to geo-blocked local content around the globe.