It’s also used by journalists, advocacy group members, and political refugees in hiding. Reuters, Fox, NBC, CNN – all of them keep open dark web channels to receive anonymous tips from whistleblowers. So, it’s only natural to find ways to keep in touch with your darknet buddies and/or customers. There are several email and IM services which you can use, and it’s highly recommended to pick one if you want to step up your dark web game. The major issue with these websites is that a whopping 50 percent are fake, and there’s no way of telling for sure if they’ll deliver or not.

Indecent Images Of Children (IIOC)
The use of the internet, social media, spyware and software to track and monitor the whereabouts of a victim and control their contact with others must be taken into account. For further guidance see the prosecution guidance Controlling or Coercive Behaviour in an Intimate or Family Relationship, Domestic Abuse andStalking and Harassment. Virtual mobbing occurs when a number of individuals use social media or messaging to make comments about another individual, usually because they are opposed to that person’s opinions. As above, the principles outlined in the prosecution guidance on communications sent by social media should be applied. In cases where certain individuals encourage others to send such messages, prosecutors should consider offences of encouraging or assisting crime under sections under the Serious Crime Act 2007. The dark web is a part of the internet that can only be accessed using specialist software and knowledge.
Related News
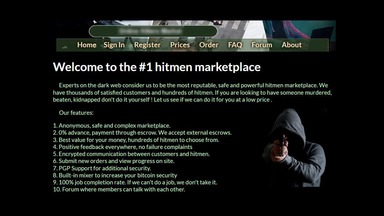
Some people will rent a mailbox to receive the shipment if they are worried that the authorities will seize it on the way to their home address. Vendors present a “blurb” about themselves and their items after the account has been protected, along with useful details like feedback rules, offers, and any bulk discounts they may offer. There are many layers of the internet that cannot be found using a search engine. Sky News has discovered potentially fake Xanax being offered for sale on social media for as little as £1. There is concern about a rising number of “dangerous fake” illicit drugs being sold as benzodiazepines, Public Health England says. To save money, you have to find the listing in the dark marketplace at the most reasonable price, and it’s not that easy as it probably seems to be.

Combine Tor With VPN
That goes for more than hot takes on social media or embarrassing college party pics. Once the info leaves your device, it will likely languish in a database before being sold to a data broker as part of a package. Now that you know how criminals plan to use your data, you need to find out what information they already have. To do this, you can use a dark web scanning tool from a personal data removal service. Many password managers also include dark web monitoring as part of a paid subscription.
See Your Digital Footprint With A Dark Web Scanner
- Engaging or even just browsing can lead to serious legal consequences.
- It sounds mysterious, slightly sinister and is becoming more widely understood, but how much do you know about the ‘dark web’?
- Williams said that personally targeted scams are rare partly because cybercriminals are lazy.
- Investigators and prosecutors need to be able to co-ordinate their approach and respond quickly to developments and opportunities to disrupt or prevent illegal activity, obtain evidence and make arrests.
- You can choose the best darknet (.onion) website that suits you and start surfing.
- Here are some examples of dark web prices based on data from Statista and Merchant Fraud Journal.
Under section 8 possession or making or supplying articles for use in frauds includes any program or data held in electronic form. Some social networking sites may disable false accounts when they became aware of them. Cyber-enabled fraud is possibly the most common of all cybercrime offences.
Illegal Firearm Offences Related To The Dark Web
A number of investigations to identify additional individuals behind dark web accounts are still ongoing. Sure, it’s not as secure as the clear web version, but it’s there and totally legal to use. Hidden Facebook is hardly the only social media client on the dark web. If you make use of a password manager, then it may come with a feature that monitors the dark web for mentions of your email address and password, or any other personal details. It’s something built into the password management services offered by Apple and Google as well, so you don’t need to trawl through data leaks manually yourself.
Virtual Private Network (VPN)

However, the dark web was soon utilized by other groups like drug dealers, weapon traders, and other malicious and illegal corporations, which changed why the dark web was designed. The purpose of creating it is to provide a platform for intelligent agents and whistleblowers to report wrongdoings or expose crimes surrounding them while staying anonymous. Some secure services even use escrow services to gain trust and keep the doubts of scams away. Even though you can access the dark web securely with Tor and VPN combo, there are other dangers that you need to stay vigilant to avoid getting trapped with them. This website uses Google Analytics to collect anonymous information such as the number of visitors to the site, and the most popular pages.
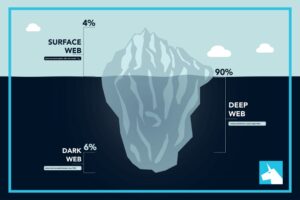
In some countries, such as China and North Korea, the government uses heavy online censorship and blocks many dark web websites. This is where an Onion website, like the Tor browser, comes in handy. It is the dark web’s version of Wikipedia with a massive links directory.
“Blatant Disregard Of Restraining Orders Will Carry Serious Consequences”, The Crown Prosecution Service Warns
Journalists, political activists, and whistle-blowers have often used it as a refuge to communicate and share information without the fear of persecution. If personal data such as your National Insurance Number, bank details or passwords are found on the dark web, take immediate action to protect yourself. Place a credit freeze or lock on your credit reports, monitor your credit reports and financial accounts closely for any unauthorised activity, and consider enrolling in a credit monitoring service.
The Bitcoin was then broken down into smaller amounts and transferred through the “Bitcoin Fog”, before being moved to other public addresses in an attempt to hide the trail of the money. “I’d always advise people to be very careful what you put out there,” Williams told me. “If you’ve posted anything online, it’s already out there. You can’t put the genie back in the bottle.” Companies often sell off customer data during an acquisition or as part of bankruptcy settlements. In these cases, your data gets packaged up and sold to another company, as seen in the recent 23andMe buyout by Regeneron Pharmaceuticals.

The Obscene Publications Act 1959 (‘OPA’) was amended to deal with electrically stored data or the transmission of that data. Transmitting comments to another person in the context of an internet relay chat is publication, even if there is just one recipient and one likely reader of the article. If the publication is obscene, prosecution under the OPA can be considered. For further guidance, prosecutors should refer to the prosecution guidance Obscene Publications. The use of cyberspace and the variety of digital tools available has further facilitated the taking, making, showing and distribution of indecent images of children.
Investigators and prosecutors need to be able to co-ordinate their approach and respond quickly to developments and opportunities to disrupt or prevent illegal activity, obtain evidence and make arrests. Consideration should be given as to whether a Joint Investigation Team (‘JIT’) is appropriate. Digital evidence and communications data can also be obtained directly from Communication Service Providers (‘CSPs’) as well as from computers and digital storage devices. Investigators have the power to serve orders on CSPs that oblige them to disclose communications data. Many CSPs are based in the US and may be obtained through Mutual Legal Assistance (‘MLA’, see below). Developments in technology have also created a new landscape for controlling, sexually-motivated or other forms of interpersonal relationship offending.
If you buy 10 grams of hash from a European vendor for $41.35, you’ll likely receive low-quality stuff. On the other hand, dealers from Pakistan and Afghanistan sell top-notch hash for this or even lower price. The one which came from the UK cost about $3 per gram and was the worst hash I ever tried – a pale-black waxy substance with a little THC. I paid for the resin from the Asian country $2 per gram and was pleasantly surprised at its potency and fragrance. You’d better always favour domestic dark web trusted vendors over overseas ones for three reasons. Firstly, national orders will hit your post box faster than international.
Law enforcement agencies keep an ear to the ground on the dark web looking for stolen data from recent security breaches that might lead to a trail to the perpetrators. Many mainstream media organizations monitor whistleblower sites looking for news. Dark web websites look pretty much like any other site, but there are important differences. That’s “a special-use top level domain suffix designating an anonymous hidden service reachable via the Tor network,” according to Wikipedia.