On top of that, the installation process of Freenet is rather easy. Simply download the file, install the software, and you’re ready to use its web-based interface. In opennet mode, the network will automatically assign you to other users on Freenet’s network.
Use The Right Tools: Tor And Beyond
One of the most well-known places people want to visit is the Hidden Wiki. However, the Hidden Wiki is a generic name used by several directories. I’ve put together 10 of the best dark websites I have personally used, but if there are any websites I have missed, please feel free to put them in the comments below.
Report It To The Authorities (if It’s Safe To Do So)
Insights like these help researchers and advocates understand how and why Tor is being used. With this info, the wider online community can grasp Tor’s impact and its ability to provide secure and anonymous internet access. Although Hidden Answers offers an outlet for anonymous dialogs, users should stay cautious while browsing. Posts on controversial or even illegal topics are fair game, so the Tor website is a double-edged sword.
- One of its most concerning impacts is the sale of stolen data, including personal information, financial credentials, and intellectual property.
- The open web, also called the surface web, includes any public web content that is indexed by search engines.
- The results from your search are always neutral, too (unlike Google, which is sometimes known for being biased).
- I found it especially useful for testing new services without risking my main email address, though messages expire after 24 hours.
News, Media, And Other Information Organizations
The ethos of Hidden Answers lies in the belief that free access to information and unbridled expression are fundamental human rights. By providing a space where questions can be asked and answered without judgment or identification, the platform embodies the principles of free speech and informational freedom. However, the anonymity and lack of oversight also present challenges, such as the potential for misinformation, and illegal activities.
Private Internet Access
SecureDrop is a site that protects the privacy of journalists and whistleblowers. It allows you to search for images, maps, files, videos, social media posts, and more. Even without monitoring your browsing activities, DuckDuckGo will offer decent answers to your questions. Apart from the dark web markets that are operating online today, some raided platforms influenced many markets. It has a bidding feature, with new batches of stolen data being frequently added.
Her side gig is an arts and culture blog, ‘Some Notes from a Broad’. And when not wrangling bits and bytes into words, Rosalyn enjoys low-fi hobbies like reading books, walking her Whippet Sketch, and having one too many coffees at her favourite café. Where it’s legal, accessing the dark web can serve legitimate purposes for threat analysts, privacy advocates, and security practitioners. Increasingly, privacy-focused coins such as Monero (XMR) and Zcash (ZEC) are being adopted to protect anonymity and make tracing funds difficult for law enforcement.
Access The Dark Web Safely
For more information, read more about the most secure email service providers in my other post. Then, simply click the operating system that you are using and download the file. While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store. So, once you’ve activated your VPN and your privacy is secured, it’s time to visit Tor’s official download page. Make sure that when you download the Tor file, it’s from their official website. It’s impossible to access the dark web with a regular browser like Chrome or Safari.
Choose A Dark Web Search Engine
This way, if you’re interested in a specific topic, you can find it quickly. As the digital world continues to evolve, the Dark Web will undoubtedly remain an important and often controversial part of the internet’s landscape. Whether used for good or ill, its shadowy nature is unlikely to fade anytime soon. One of the most famous examples is WikiLeaks, the international organization that publishes classified and sensitive documents. WikiLeaks uses the Tor network to allow whistleblowers to submit confidential information securely and anonymously. The dark web has flourished thanks to bitcoin, the crypto-currency that enables two parties to conduct a trusted transaction without knowing each other’s identity.

Verified Social Channels And News Sites
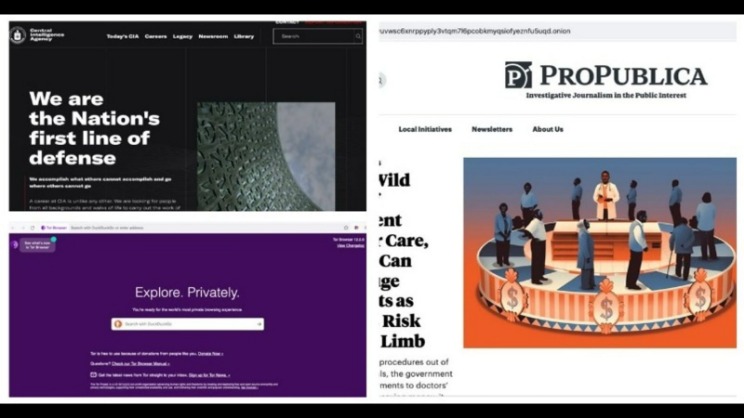
Riseup’s services can be accessed on the surface web or via Tor websites if users want to protect their anonymity. A large portion of activities on the dark web involve illegal content, transactions, or services. Simply accessing certain sites or engaging with the wrong links could implicate you in criminal investigations. Accessing the Dark Web, a part of the web that isn’t indexed by standard search engines, is not illegal in most countries. People use it for various legitimate reasons, such as bypassing censorship in restrictive countries.
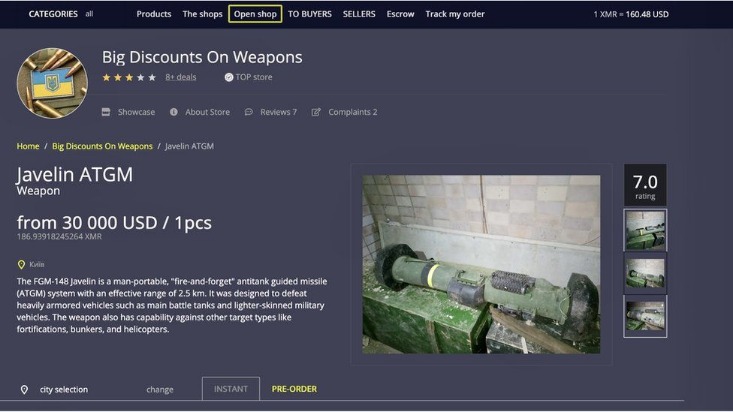
From a statistical standpoint, this collective of websites and data makes up under 5% of the total internet. Many dark web marketplaces are scams designed to exploit unsuspecting users. Without regulated oversight, buyers risk losing money or, worse, exposing their identities to cybercriminals. If you only want to mask your IP address and don’t need to access the dark web, then going online with a VPN is much easier and faster than using Tor.
If you’re intrigued and want a firsthand experience, follow this guide to learn how to access the deep web with an anonymizing browser. We’ll use the Tor browser for this guide, but any other browser that supports the Tor protocol will do. Learn how CrowdStrike can help protect your brand and data with CrowdStrike Falcon® Adversary Intelligence. If you discover your data on the dark web, act quickly to minimize the damage and report the incident to relevant authorities to ensure any necessary legal action is taken.
This disables potentially dangerous features like JavaScript that could reveal your identity. NoScript and HTTPS Everywhere extensions provide additional protection against malicious scripts and unsecured connections. Proton Mail’s dark web version provides end-to-end encrypted email with enhanced privacy protection.