That means you may violate copyright laws while downloading books, so use a VPN to protect yourself from any legal repercussions if you have a dire need to use it. The Imperial Library currently holds around 1.5 million books, some of which may be hosted illegally, and thus, their consumption might violate copyright laws. To protect yourself against any legal repercussions, you should consider using NordVPN. Proton also offers other security tools besides ProtonMail, such as Proton Drive, Proton Pass, Proton Calendar, and Proton VPN. This service lets you create your unique domain name with the letters or words you prefer.

However, there are some significant variances in the background despite the similarities. For example, Whonix’s virtual workstation machine connects to the internal virtual LAN. It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address. Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved. Think of Tor as a regular browser like Firefox, Google, or Safari. The only difference is that it passes your traffic through random nodes before reaching the destination.
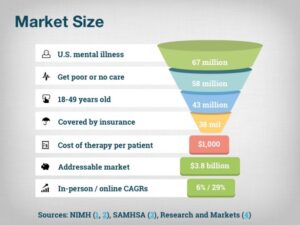
Why Is Certified Ethical Hacker (CEH V13 AI) So Popular
Also, you can set a strong password to protect your message and choose how long it will take to expire. The good news is that the platform will not see what you copy/paste. Your data is encrypted in the Tor browser before reaching the ZeroBin servers. ZeroBin is a wonderful way to share the content you get from dark web resources.
Cerebral Hidden Gems

These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies. Viruses, ransomware, and other types of malware are more common on onion sites than on the normal internet. Many pages have poor encryption standards and no other protections, so simply visiting a Tor site can infect your device. All the dark web websites we’ve listed in this article will not be of much use to you unless you know how to access and use the dark web.
Shuttered Dark Web Marketplaces
Its decentralized community structure makes it one of the best forums, and its security measures help it to withstand threats like DDoS attacks. Ideally, the forum operates within the Tot network, enhancing user anonymity. The forum is meant to host several sub-communities to assist threat actors in easily connecting with each other and finding the information they need. Most of the illegal information and data shared on this forum is related to data leaks, as well as the selling of data freely.

How To Find Links
If the above average Joe’s explanation isn’t enough for you, below are some legitimate reasons to use the Dark Web in a bit more detail. It’s important to note that although the dark web has many valuable services, it is also a hangout for cybercriminals. Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions. Therefore, the legality of the dark web will mainly depend on how you use it. You can quickly get into trouble for acting illegally, such as infringing on other people’s safety and freedom.
Following the NYT, the BBC launched a dark web “mirror” of their international edition in 2019. Note that some features of the normal website are not available on the .onion version, including BBC iPlayer. Exactly as the name suggests, what weird, crazy, interesting pages have you found? Trying to broaden views of the dark Web and see that it’s not just about marketplaces. Radar Rundown Ad blockers are the best protection against disruptive ads.
- Relays help route traffic securely by passing encrypted data through multiple nodes before reaching its destination.
- Besides, victims of crime may want to hide their identities from their perpetrators.
- Some countries and ISPs may try to prevent access to DuckDuckGo’s direct link.
- It encrypts your connection to prevent outsiders from being able to read your data and masks your IP address with one from a VPN server—so whoever’s looking can’t get any useful information.
- Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS.
What Kind Of Content Is On The Dark Web?

This just involves turning on your VPN before you open Tor and connect to dark web sites. Founded around 1999 by activists in Seattle, it has since grown to over six million users worldwide. It publishes a newsletter in multiple languages and not only runs onion services for its website but all its email and chat services. Facebook is aware of attempts by many governments to restrict access to a tool that allows strangers across the web to talk and collaborate freely. While its .onion address doesn’t make it much easier to maintain an anonymous account, it does make Facebook more accessible in places where it’s censored. Search engines on the dark web are a bit of a contradiction because dark web sites by definition are not indexed by traditional search engines.
These layers upon layers give this network its iconic “onion” name—as the onion itself has layers upon layers. However, please note this article is for research and educational purposes only. The dark net is full of notorious hackers, scammers, malware, and other viruses. We recommend using NordVPN and a robust antivirus like TotalAV to keep you safe while browsing the dark web. Switzerland-based Proton (formerly ProtonMail) is one of the most secure email services, and has a reputation for not logging IP addresses.

Download the Linux version from torproject.org, extract the file, and run the start-tor-browser script. The “VPN-over-Tor” approach offers added protection, even if Tor is compromised. By encrypting communication before it gets to the Tor network, pairing Tor with a VPN gives a second degree of protection.
Accessing Onion Sites On Android
This helps support our work, but does not affect what we cover or how, and it does not affect the price you pay. Neither ZDNET nor the author are compensated for these independent reviews. Indeed, we follow strict guidelines that ensure our editorial content is never influenced by advertisers.
Your real information could be exposed at these nodes, allowing third parties to intercept your dark web activity. That’s why we recommend connecting to VPN before accessing Tor—VPN encryption protects your data, and changing your IP adds an extra layer of privacy to protect you. When you try to connect to a .onion website, Tor will route your traffic through three or more randomly chosen nodes before it reaches your destination website.
Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. In darknet mode, you can select friends on the network and only connect and share dark web content with them. This enables individuals to form groups and only share content in a highly anonymous network of darknet users who they know.
Moreover, stolen credit card markets such as BrainClub and BidenCash used to advertise on XSS. Its regular users claim that its longevity and popularity were a result of its overseas management and a strong admin handling of the operational security (OPSEC). Fortunately, on July 22, 2025, French police reported arresting a key XSS administrator after a long-running investigation, and the forum was seized. Also, it provides users with an escrow service, which adds an extra layer of trust when they conduct transactions on this notorious platform. Nulled is an enduring forum that specializes in nulled leaks, cracked software, and premium account access.
The majority of the web is called the “deep web” (often referred to as the “invisible” or “hidden” web). The deep web is basically all the content that you can’t find using Google or Yahoo search. So, that means that the number of pages increased by over 100 trillion in just over three years. Hypothetically speaking, Google may be aware of well over 200 trillion individual pages (these are obviously NOT all indexed in the search engine). So, sites that contain a domain extension like .com, .org, .net, .biz, .info, etc. can be found on the surface web. In addition, the content on the pages don’t need any special or custom configuration to access.